28.4k views
Device Endpoint Security (DES) is a set of technologies designed to help organizations protect their mobile devices and applications from malware threats. DES provides comprehensive protection for iOS and Android smartphones and tablets, including the ability to wipe them if they become infected with malware remotely.
DES was originally developed to protect servers and desktops, but it also protects mobile devices. In addition, DES can be used to secure cloud services and networks.
The term “device” refers to any computing device that connects to your organization’s network, whether a smartphone, tablet, laptop, desktop computer, or other devices. The term “endpoint” refers to the point you connect to the Internet.
A device endpoint security solution protects your organization’s business-critical information by scanning all incoming and outgoing traffic on your company’s network. It can be used to monitor any device that connects to the corporate network, such as laptops, desktops, servers, printers, and other networked devices. A device endpoint security solution monitors these connected devices for signs of suspicious activity and alerts you immediately if anything goes wrong.
Device Endpoint Security works by scanning all incoming messages and emails for potential malware threats. If a message contains one of these threats, the system will automatically remove the threat before allowing you to read the message. The exact process applies to attachments sent via email.
When you connect to the Internet, your computer sends requests for websites, e-mail messages, and programs. All of these communications pass through your computer. If someone hacks your computer, they can intercept them.
Device endpoint security works like an antivirus program. It monitors all of your incoming and outgoing communications, and it stops the communication whenever it finds something suspicious.
Device endpoint security doesn’t just monitor connections to the Internet, it also monitors connections to your local area network (LAN). This means it can detect viruses on your personal computer, such as those in documents, pictures, music files, etc.
Mobile devices have become more than just personal tools, and they’re now essential parts of our lives. As such, we need to make sure they’re secure. That’s where Device Endpoint Security comes in, and it protects your mobile devices from malware infections, which could lead to identity theft, financial loss, and other problems.
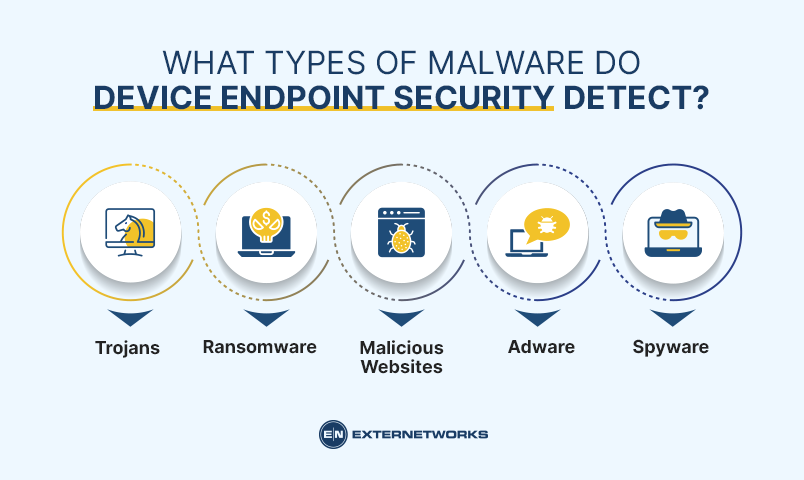
Device Endpoint Protection detects several different kinds of malware:
Trojans – Trojans are programs that perform actions without your knowledge. They might install additional spyware on your phone or tablet, steal confidential information, or cause damage to your device.
Ransomware – Ransomware is malware that locks up your files and demands money to unlock them.
Malicious websites – can contain harmful code that can harm your device. For example, they can redirect you to fake banking sites or download dangerous apps onto your phone or tablet.
Adware – Adware displays annoying ads on your screen. Some adware may collect sensitive information about you, like your search history and browsing habits.
Spyware – Spyware collects information about you without your permission. It might monitor your keystrokes, track your location, record conversations, and take screenshots.
Device endpoint security is important for many reasons. First, it prevents hackers from accessing sensitive information. Second, it stops them from spreading viruses and malware. Third, it prevents them from stealing confidential data. Fourth, it reduces downtime by preventing system crashes. Finally, it improves productivity by reducing errors.
Yes, you need endpoint security. Hackers will try to steal your data, infect your system, or crash your computer. And even though you can stop them from doing these things, you can’t always stop them from getting past your firewall. You need device endpoint security installed on every device connected to the Internet.
No, device endpoint protection won’t slow your computer. Device endpoint protection uses the same technology used by antivirus programs, and it quarantines the virus when it detects a virus, and this process takes only seconds.
Endpoint security protects against malware, phishing scams, spyware, and viruses. It also prevents users from accessing sensitive information stored on the device. The most common way to attack a computer system is through a virus or worm that spreads across networks. By installing endpoint security, you can stop this kind of attack before it starts.
Endpoint security protects devices when they connect to networks, whereas endpoint protection protects all devices connected to those networks. For example, if you have a laptop connected to a Wi-Fi network, both endpoints would be protected by the same software. But if you have a desktop computer connected to a wired Ethernet port, only the endpoint protecting the Ethernet port would be protected.
An endpoint is a device connected to another networked device, such as a router or switch. An endpoint may also refer to the physical port to which the device is attached. The term “endpoint” comes from the fact that it’s at the end of a cable (or other connection).
Endpoints are often used for connecting devices to networks and/or Internet Protocol (IP) networks. For example, a computer might have one or more Ethernet ports connecting to a different network segment. A single Ethernet port could connect to a local area network (LAN), while two Ethernet ports could connect to a wide-area network (WAN). Similarly, a modem or fax machine could use a telephone line to connect to a WAN, while a printer could use a parallel port to connect to a LAN.
In conclusion, device endpoint security is an essential tool in any business or personal computer, and it helps keep your devices safe from hackers and other threats. If you want to learn more about how you can use device endpoint security, visit our website. We hope you find our site helpful!
