28.4k views
Malware is software designed to damage or disable computer systems without the owner’s knowledge. The term comes from malicious (harmful) software. In other words, Malware is software that does something wrong.
Malware has become a significant problem for businesses and consumers alike. According to Symantec, over $1 trillion worth of damage was caused by cybercrime last year alone. Malware attacks are becoming more sophisticated and harder to detect, and this means that even if you take precautions, you might still fall victim to malicious software.
Malware is malicious software that steals information from computers. Viruses are programs that make changes to your operating system. You may never know you were infected. Malware includes anything that harms or hacks users.
It could be stealing personal data, causing damage to computers, or even causing physical harm. It doesn’t matter what the motivation behind the hacking is, as long as the hacker intends to harm someone.
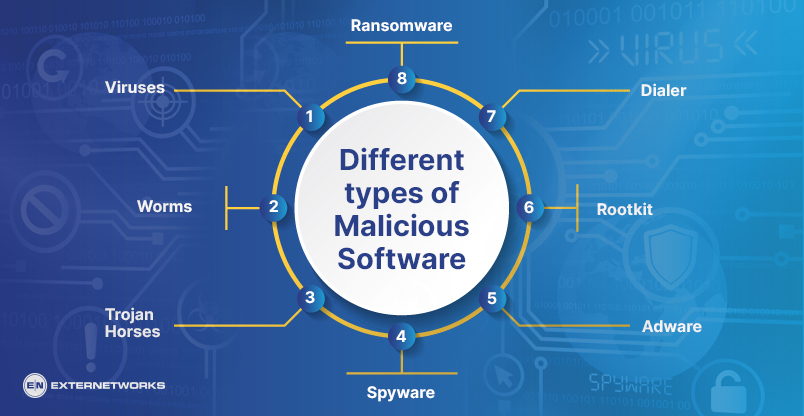
Malware can come in many different forms. Some examples of Malware are listed below:
Viruses spread quickly because they can replicate themselves. Once a computer becomes infected, the virus may remain dormant until activated. When activated, the virus replicates itself and attempts to infect other computers.
A worm is similar to a virus but is usually much smaller. Unlike self-replicating viruses, worms have a life cycle that needs to be passed from one host to another. Worms can cause problems by deleting files, corrupting data, or slowing down a computer.
A trojan horse is a program that appears harmless but contains hidden Malware. Trojans are often disguised as games, screensavers, or applications that perform legitimate functions. Because these programs appear normal, users may download and install them unknowingly.
Spyware is software that secretly monitors what you do online and sends information about your activities back to the person who wrote the software. Spyware can monitor everything from your web browsing history to your search queries. Spyware can also record your keystrokes, take screenshots, and track your mouse movements.
Adware software displays advertisements when you visit certain websites. The ads may offer free services or products, and this software is typically bundled with other programs. Some browsers include an advertising toolbar that automatically loads each time you start up the browser.
A rootkit is a malicious program that hides itself to be challenging to detect. Rootkits are used to hide illegal activity. For example, hackers may use rootkits to conceal their identity while committing fraud.
A dialer is a program that allows someone to make phone calls using a computer. Dialers are often used to send spam messages.
Ransomware is a type of malicious software that locks all or part of a user’s computer. It encrypts the hard drive and then demands payment to decrypt it. Ransomware can lock a file or entire operating system.
There are many ways to detect Malware. The most common way is through antivirus software, and Antivirus software scans for known malware signatures and removes them. However, this method does not work against all Malware.
Another way to detect Malware is through behavioral analysis. This means looking at how an application behaves when it runs.
For example, if an application opens a file for no apparent reason, it could be suspicious behavior. If an application has a lot of activity after midnight, it could be a sign of something going on.
Businesses should focus on preventing breaches by securing the perimeter. Advanced Malware must be detected and stopped before it can cause damage. High-level network visibility and security intelligence help ensure that advanced Malware doesn’t get past perimeter defences.
The best way to protect yourself from malware infection is to avoid downloading suspicious programs. If you receive an email attachment, you should never open it unless you know what it is. In addition, you should not click on links in unsolicited emails and delete the message immediately.
Finally, you should ensure that any software is downloaded directly from its official website. There are several ways to stop malware infection. One is to use antivirus software. Antivirus software can scan a computer for known malware signatures. However, there is no guarantee that the signature will match the actual Malware. Therefore, antivirus software cannot always identify Malware.
Another way to prevent malware infection is to use firewalls. Firewalls can block Malware from accessing the network, and they can also filter out traffic based on its source and destination. Network administrators can set up rules to allow only approved traffic to pass through the firewall.
Malware is advanced, and it can be disguised as regular programs or even as other types of Malwares. It can test for conditions of a sandbox meant to block malicious files, and it can try to fool security software into thinking it is not harmful. Advanced malware protection software helps prevent, detect, and efficiently remove threats.
