28.4k views
Have you ever heard of an account takeover attack? It’s a term that is becoming increasingly common in the world of cybersecurity. But what exactly does it mean, and why should you be concerned about it?
In today’s digital age, our personal information is stored in various online accounts, from social media platforms to banking websites. Unfortunately, cybercriminals have found ways to exploit these accounts and gain unauthorized access, putting our sensitive data at risk.
Understanding the definition of an account takeover attack is crucial to protect yourself and your online identity. By familiarizing yourself with the tactics used by hackers and the potential consequences of such attacks, you can take the necessary precautions to safeguard your accounts and prevent becoming a victim. So, let’s explore the world of account takeover attacks and their potential dangers.
An ATO attack involves an unauthorized user gaining access to another person’s online accounts without their knowledge or consent. Account takeover attacks can target any type of organization, from large enterprises and financial institutions to small businesses and even individual users.
In order to gain access to someone’s account, hackers typically use a variety of tactics, including stolen credentials or compromised usernames and passwords. In some cases, phishing attacks are used to access an organization’s systems or accounts. Another way to access someone’s account is through social engineering techniques, such as pretexting or identity theft.
Historically, financial institutions were the targets of choice for these types of attacks because of their role in handling sensitive user data. Now, however, any organization with a user-facing login is at risk.
The most prevalent motive for these attacks is still financial gain – cybercriminals want cryptocurrency and personal data to resell on the dark web, or even trick victims into installing ransomware. In other cases, cybercriminals may be more interested in obtaining PII (Personally Identifiable Information) to carry out identity theft and commit insurance fraud or access lines of credit.
Organizations must take proper precautions to protect their users from falling victim to an ATO attack; this includes stronger passwords and authentication requirements, timely updates to networks and systems software, and consistent monitoring of systems logs for suspicious activity. Protecting users from losing valuable personal information or funds starts with preventative measures put in place by the organizations themselves.
As with any type of cyber attack, the consequences of an ATO attack can be far-reaching and devastating. Unauthorized access to someone’s account can lead to financial losses, as a hacker may attempt to transfer funds from one account to another. In some cases, hackers may also use an ATO attack to gain access to a company’s network and cause disruption or steal valuable data.
Some of the common consequences include:
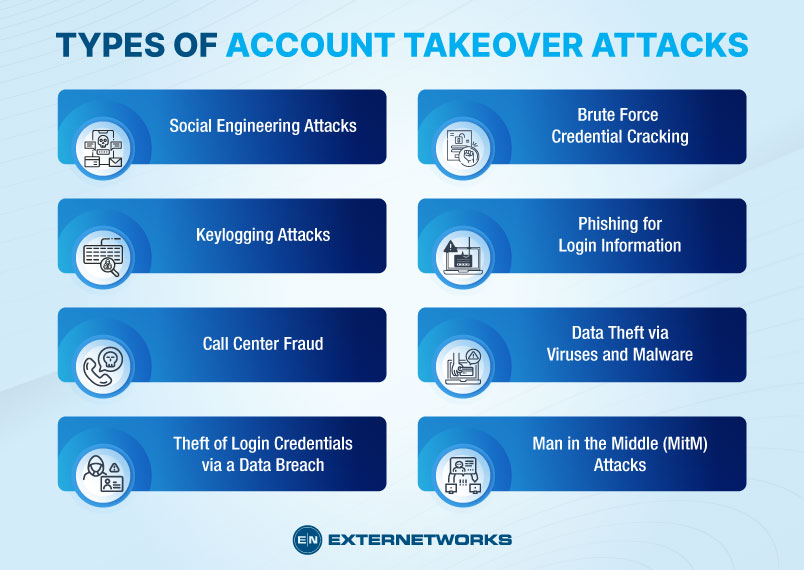
Several types of account takeover attacks are commonly employed by attackers, each with its own methods and strategies.
Social engineering attacks are another form of account takeover attack. These attacks involve using tactics such as phishing and deception to gain access to someone’s accounts.
For example, hackers may trick someone into revealing their usernames and passwords or install malicious software on the victim’s computer.
Keyloggers are tools that can record every keystroke that you type into a computer or mobile keyboard. Keyloggers can record much information about your activity because you interact with a device primarily through the keyboard.
Keyloggers are spread in different ways, but all have the same purpose. They all record information entered on a device and report it to a recipient. Let’s take a look at a few examples showing how keyloggers can spread by being installed on devices:
Hackers have the ability to insert malicious code onto web pages. If you happen to click on an infected link or visit a malicious website, a keylogger will automatically download it onto your device.
Another way a keylogger can be installed is by an email attachment. Hackers may send you an email containing a malicious file, which will install the keylogging software once opened.
The DarkHotel attack is a keylogger that uses malware. It targets unsecured hotel Wi-Fi and tricks users into downloading the software. Once downloaded, DarkHotel records keystrokes and sends them to the hackers. After a certain number of keystrokes, DarkHotel removes itself to avoid being detected.
Call center fraud is a type of account takeover attack that involves criminals calling into customer service centers in an attempt to gain access to customer accounts. The attacker may pose as the legitimate customer and attempt to have their account credentials reset or modified.
Data breaches involving unauthorized access to secure information and data have become increasingly common in recent years. Many of these breaches are targeted at compromising user login details such as usernames and passwords.
Cybercriminals acquire this data through various means including hacking into systems or databases, buying stolen credentials from the dark web, or skimming username and password information from phishing websites.
Once these malicious actors obtain a user’s credentials, they don’t just use them on the website from which they originally acquired them–they will also attempt to access other accounts owned by those same users utilizing the same username and password combination.
By doing so, cybercriminals can leverage compromised users who employ poor login practices such as reusing weak passwords across multiple websites or services and gain access to extensive personal information profiles that victims may not even be aware exists about themselves online.
One of these is credential cracking, also known as brute force attack or dictionary attacks. This process involves attempting various passwords to discover which one is correct.
To speed up the process, hacking tools generate automated bots that can test an extensive list of password combinations quickly. Accounting for current software available for hackers, 8-character passwords can be broken in less than an hour.
Phishing attempts involve cybercriminals sending emails, messages, or even setting up fraudulent websites to capture login data. This usually involves creating a seemingly legitimate email that looks like a familiar organization or person has sent it. The email may contain a link asking users to log in to verify their identity or receive important information.
Viruses and malware have various functions. They often steal information from your device. Many viruses track keystrokes, capturing passwords, while others spy on your browser to hijack bank details. Antivirus software can prevent this.
Internet traffic passes through multiple servers before reaching a website. If someone intercepts your unencrypted traffic, they can see everything you do online, including your login details. Man-in-the-middle attacks often occur through home routers or public Wi-Fi networks. To protect yourself, use trustworthy VPN software.
A comprehensive fraud detection system offers financial institutions a clear view of user activity during the transaction process. An effective defense involves monitoring all activities on a bank account, as cybercriminals typically engage in various actions, such as creating a payee, before attempting to withdraw funds.
By closely monitoring all activity on an account, one can identify patterns of behavior that indicate the potential for account takeover fraud.
In order to protect yourself and your organization from ATO attacks, it is essential to have robust security measures in place.
This includes implementing strong authentication methods, such as two-factor authentication, and regularly changing passwords. Additionally, having an effective incident response plan can help you detect suspicious activity and respond quickly in case of an attack.
Finally, it is important to stay current on the latest security trends and educate your staff about best practices for protecting their accounts.
The best way to protect yourself from account takeover attacks is by taking the necessary precautions to safeguard your accounts. Here are a few tips that may help:
Furthermore, companies should maintain a list of compromised accounts and promptly notify affected users to protect their financial and personal details like social security numbers. Investing in insurance fraud protection can also mitigate losses resulting from account takeovers.
Conclusion
Account takeover attack can be devastating for both the victim and the company, as they can lead to financial losses and a damaging reputation. By taking the necessary precautions and being aware of potential risks, companies and individuals alike can help protect themselves against account takeover attempts and minimize their chances of becoming victims.
It is important to ensure that secure authentication measures are enabled on your accounts, monitor for unusual activity, and use a trusted VPN when accessing public Wi-Fi networks. Additionally, companies should invest in customer support protocols to quickly respond to compromised data events. Organizations should ensure that they have the appropriate security measures, such as Multi-Factor Authentication and robust customer support protocols.
At ExterNetworks, we understand the importance of staying one step ahead in the ever-evolving landscape of cyber threats. With our proactive monitoring services, you can rest easy knowing that potential threats are being identified and addressed before they can impact your organization. Our team of cybersecurity experts brings years of experience to the table, ensuring that your systems are always protected against the latest threats.
We offer customized solutions to fit your unique cybersecurity needs, ensuring you receive the level of protection your organization requires. Additionally, we help keep your organization compliant with industry regulations and standards, giving you peace of mind knowing that your data is secure.
By choosing ExterNetworks for cyber threat monitoring services, you can save on the costs of hiring an in-house security team while benefiting from top-notch protection. Don’t wait until it’s too late—contact ExterNetworks today to learn more about how our services can benefit your organization.
