28.4k views
A connectionless protocol is a type of network communication where data packets travel independently through multiple nodes without being routed or directed. Connection-oriented protocols require a direct path between two hosts before sending data. Read the below article to know more about connectionless protocol.
Connectionless protocols are used to transmit data over networks without using a central server. They are also called peer-to-peer (P2P) protocols because they allow multiple computers to communicate directly.
A connectionless protocol allows two or more devices to exchange information without going through a third party. No single point of failure exists. If a device goes down, another device can take its place. It’s like the telephone system where you didn’t have to dial someone who was already on the line.
Connectionless protocols are often used in many different kinds of applications. For example, computer games use them to connect players together, and Peer-to-peer digital music stores use them to share files.
The Internet Protocol (IP) is one of the most common connectionless protocols. It is designed to send messages from one device to another, and it’s useful for connecting all types of devices.
The Transmission Control Protocol (TCP) is an important component of IP. TCP is responsible for ensuring that the data sent between devices reaches its destination in the correct order. There are three main components of TCP:
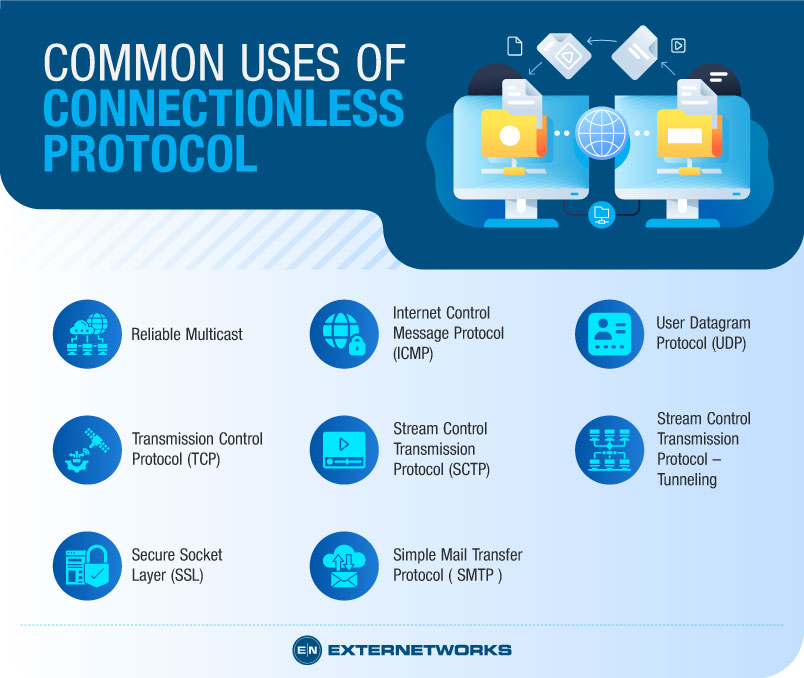
A connectionless protocol is one of the most basic forms of communication which does not require any sort of connection to send data across it. These protocols are often referred to as unreliable because they do not guarantee the delivery of packets and hence cannot be relied upon for reliable communications. In this section, we will discuss common uses of connectionless protocols.
Reliable multicasting requires datagrams sent to several recipients simultaneously. If a recipient drops the packet, the sender must resend the packet. With connectionless protocols, there is no way to determine whether a packet was received successfully. These protocols should only be used when reliability is not required.
Internet Control Message Protocol ( ICMP ) is an older IP version but has been retained due to backward compatibility reasons. It is used to determine the availability of hosts on the internet. This protocol works on a hosted basis rather than a router basis. Each host sends a message to each other, informing them about their current status. A host may fail to respond to a ping request, indicating that the other host is inquiring about their status. The destination host replies with its status, and the source host informs the originator of the status.
UDP is used in communication paradigms like Simple Network Management Protocol(SNMP). UDP provides guaranteed sequential delivery of messages between two hosts. It does no form of error detection or retransmission. UDP is primarily used for transferring audio streams.
Transmission Control Protocol ( TCP ) and User Datagram Protocol ( UDP ) are the two main components of the TCP/IP suite. TCP is responsible for ensuring reliable delivery of data and guaranteeing full-duplex connections. On the other hand, UDP is used to transfer small amounts of data across a network and does not have any built-in mechanisms to ensure the reliability of data transmission.
Stream Control Transmission Protocol ( SCTP ) is a hybrid protocol based on TCP and UDP. Like TCP, SCTP provides reliable, ordered, and multiplexed stream connectivity between peers. Unlike TCP, however, SCTP can operate over unreliable networks and reliably over point-to-point links.
Stream Control Transmission Protocol ( SCTP ) is a tunneling protocol that allows a single connection to carry multiple logical connections simultaneously. With SCTP tunnels, a single connection can be shared among different applications. For example, if you need to transfer large files from your client machine to another server, you can create a single SCTP connection and share it among all the programs you want to send the file through.
A secure Socket Layer ( SSL ) protocol establishes secure communications over a non-secure communication channel. In other words, SSL encrypts data being transmitted over a normal socket.
Simple Mail Transfer Protocol ( SMTP ) is a protocol that handles the exchange of email. It is used to send mail across the Internet. To connect to a remote system using this protocol, you must first set up a mail account on the remote system. You then compose the mail and send it to the remote address provided in your mail program. When the recipient receives the mail, they will read it in their email application and reply to you.
In conclusion, connectionless protocols transmit data packets without requiring the sender and receiver to establish prior knowledge about each other. These protocols do not guarantee the delivery of messages to the destination. Instead, these protocols rely on packet re-transmissions to ensure message delivery.
