28.4k views
Have you ever wondered how cybercriminals gain unauthorized access to your online accounts? The answer lies in a technique called credential stuffing. In today’s digital age, where our personal information is at constant risk, it is crucial to understand this method and how to protect ourselves from it.
With the increasing number of data breaches and the vast amount of personal information available on the dark web, cybercriminals have found a way to exploit this data for their malicious activities.
Credential stuffing is the process of using stolen usernames and passwords from one website to gain unauthorized access to other online accounts. It is a widespread and highly effective technique used by hackers to compromise user accounts and carry out various fraudulent activities.
As technology advances, so do the tactics of cybercriminals. Understanding the concept of credential stuffing and the methods employed by hackers is essential in safeguarding our online accounts and personal information.
In this article, we will explore the intricacies of credential stuffing, its potential consequences, and, most importantly, the measures you can take to protect yourself from falling victim to this malicious technique.
Credential stuffing is a type of cyberattack that involves the automated injection of stolen username and password pairs into website login forms. This attack method takes advantage of the fact that many people reuse the same passwords across multiple online services.
Cybercriminals obtain these username and password pairs from data breaches or phishing attacks and then use bots to rapidly input the credentials into websites to gain unauthorized access. The success rate of credential stuffing attacks is alarmingly high due to the prevalence of password reuse.
Various industries are targeted by credential stuffing attacks, including financial institutions, e-commerce platforms, and online service providers. These sectors are particularly attractive targets because they contain a wealth of valuable user information and financial data.
Firstly, the success rate of these attacks may seem surprisingly low, with only a small percentage of login attempts resulting in a successful breach.
However, when considering the vast collections of login credentials readily available to cyber criminals, even a low success rate can yield significant access to user accounts.
Modern bot technology is crucial in making credential stuffing attacks more effective. Attackers can use sophisticated bots that mimic human behavior and bypass security measures such as CAPTCHAs or rate-limiting mechanisms.
These bots can emulate various user devices, IP addresses, and even simulate regular user traffic, making their login attempts almost indistinguishable from legitimate login attempts.
Another key contributing factor is the prevalence of password reuse among users. Many individuals use the same password for multiple accounts, including sensitive ones.
To combat the effectiveness of credential stuffing attacks, organizations must implement robust security measures.
Credential stuffing attacks involve using automated bots to systematically test large lists of stolen or leaked username and password combinations against various online services to gain unauthorized access to user accounts.
But password strength does not protect against credential stuffing. These attacks rely on the fact that many individuals reuse passwords across multiple platforms, making it easier for attackers to exploit the same login credentials across different websites or applications.
Bots are programmed to mimic human behavior, bypassing security mechanisms such as CAPTCHAs or rate-limiting measures.
They emulate user devices, IP addresses, and even simulate regular user traffic, making their login attempts appear legitimate.
By automating this process, attackers can test numerous combinations at a rapid pace, significantly increasing the chances of successfully accessing user accounts.
The success of credential stuffing attacks is also fueled by the availability of breached credential lists on the dark web.
These lists, containing large amounts of personally identifiable information, including email addresses and usernames paired with corresponding passwords, are readily accessible to attackers.
This allows them to easily procure login credentials and launch large-scale attacks against a wide range of online services.
Due to the scalability and success rates of these attacks, organizations must prioritize implementing strong security measures.
To detect and prevent credential stuffing attacks, organizations need to implement effective security measures such as Multi-Factor Authentication, strong passwords, and device fingerprinting.
While some commercial web application firewalls and services use more advanced behavioral techniques to detect suspicious login attempts, website owners can take measures to prevent such attacks.
Enabling Multi-Factor authentication (MFA) is crucial in preventing credential stuffing attacks and enhancing overall security. MFA adds an extra layer of protection by requiring users to authenticate their identity using both something they know, like a password, and something they have, such as a security token or biometric verification.
Credential stuffing attacks typically involve cybercriminals using automated tools to launch brute force attacks on online services, attempting numerous combinations of login credentials to gain unauthorized access to user accounts.
Unlike traditional security measures that primarily rely on reactive detection and response, proactive threat hunting involves actively searching for signs of malicious activity before an attack occurs.
Educating employees on the risks of weak passwords is crucial in maintaining robust cybersecurity practices within any organization. Weak passwords pose a significant vulnerability, as they can easily be compromised through credential stuffing attacks.
Employees must understand the importance of creating strong, unique passwords to protect their accounts and the sensitive information they have access to.
To create strong passwords, employees should follow best practices, such as using a combination of upper and lower case letters, numbers, and special characters. Passwords should be at least 12 characters long, and avoid using common, easily guessable phrases or personal information.
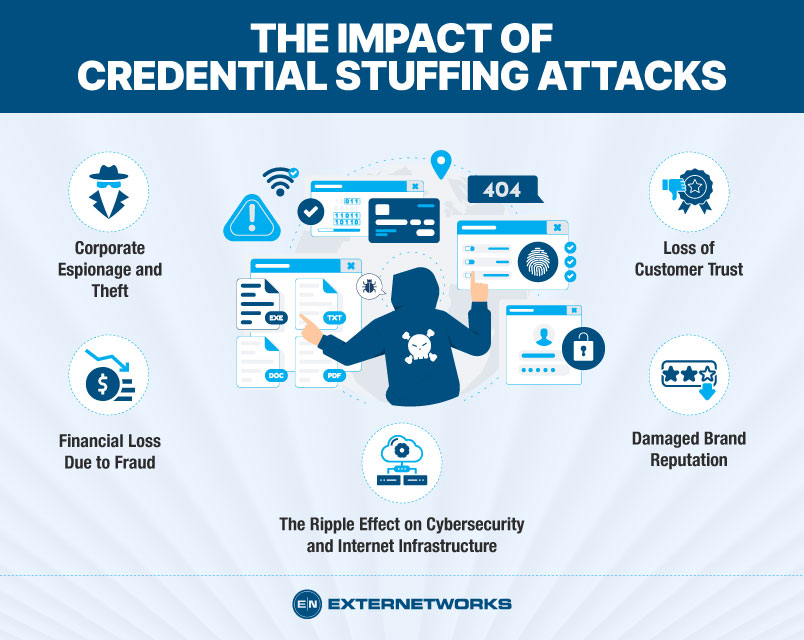
The impact of such attacks is far-reaching and can severely damage a company’s reputation and financial standing. Stolen data can be sold on the dark web, leading to financial losses for the affected business.
Moreover, the stolen information can be used by competitors to gain an unfair advantage or to blackmail the company. The loss of intellectual property and trade secrets can result in a loss of competitive edge and hinder future innovations.
Financial losses due to credential stuffing attacks can have a significant impact on organizations. Once inside, they can carry out fraudulent activities that result in monetary losses for both the targeted individuals and the organizations they interact with.
As a result, organizations may face financial losses due to the illegitimate use of their systems or services. They may face reputational damage, loss of customer trust, and potential regulatory scrutiny.
Additionally, organizations may be liable for reimbursing victims of fraud or facing legal consequences if negligence in their security practices is proven.
Credential stuffing attacks significantly impact customer trust, leaving users feeling violated and betrayed. When sensitive information, such as login credentials or personal details, is exposed during these attacks, customers can no longer trust that their data will be adequately protected by the company they have entrusted it to.
The feeling of violation and betrayal occurs because customers rely on companies to safeguard their personal information and expect a certain level of security. When a company falls victim to a credential stuffing attack, it not only demonstrates a failure to protect customer data but also raises doubts about the company’s overall security measures.
Customers may be hesitant to continue using the company’s services or providing their information in the future. The fear of having their sensitive information compromised again leads to a lack of faith in the company’s ability to safeguard their data.
A damaged brand reputation is a long-term consequence of these attacks, as it erodes customer trust and loyalty. Customers expect companies to prioritize their security and protect their personal information.
However, when a company falls victim to a credential-stuffing attack, it demonstrates a failure to safeguard customer data effectively.
The loss of trust caused by these attacks can lead to customers being hesitant to continue using the company’s services or sharing their information in the future.
This surge in bot activity can strain internet infrastructure and impact the performance and reliability of online services. The high volume of login attempts and requests from multiple IP addresses can lead to increased server load and potential service disruptions.
Businesses need to invest in advanced security measures, such as implementing stronger authentication protocols and adopting advanced threat detection systems.
As a response to the attack, your business should consider investing in advanced security measures, such as implementing stronger authentication protocols or adopting advanced threat detection systems. It’s important to note that these investments may lead to increased operational costs and put a strain on company resources.
In conclusion, it is also crucial to practice good IT hygiene by regularly updating and patching software, implementing strong password policies, and using password managers to prevent the reuse of passwords across different accounts.
Proactive threat hunting can help identify and mitigate potential attacks before they occur while educating employees about the dangers of weak passwords and the importance of following security protocols is essential in minimizing the risk of credential stuffing.
The consequences of credential stuffing attacks can be severe, ranging from corporate espionage to financial loss and damage to a company’s brand reputation. Therefore, it is imperative for organizations to address this type of cyberattack to safeguard their data, protect their customers, and maintain their reputation in the digital landscape.
