28.4k views
In today’s digital age, where our personal information is constantly at risk, have you ever wondered how hackers could intercept our private communication and gain access to sensitive data? One of the most common cyber attacks used to achieve this is the Man in the Middle (MITM) attack.
With the increasing reliance on technology and the internet, cyber attacks have become more sophisticated and prevalent. The MITM attack is a prime example of how hackers exploit vulnerabilities in our online communication to deceive and manipulate unsuspecting users.
This article provides an in-depth analysis of MITM attacks, including the techniques employed by hackers and measures to protect against this cyber threat. By understanding the mechanics and potential consequences of MITM attacks, individuals can ensure a more secure online experience.
A man-in-the-middle attack (MITM) is a deceptive attack that can steal confidential information, like account details and credit card numbers, by pretending to be a legitimate user.
The attacker positions themselves between the real user and the application they are using. This enables them to listen in on the conversation or pretend to be one of the participants, making their malicious activity appear normal.
The consequences of a MITM attack can be challenging to recover from and can vary significantly depending on the intercepted information. The malicious actor could use this stolen data for identity theft, unapproved fund transfers, illicit password changes, or even gain a foothold inside secured networks to launch advanced persistent threat (APT) assaults. It’s important for users to understand the potential risks associated with this type of attack so they can protect themselves from falling victim.
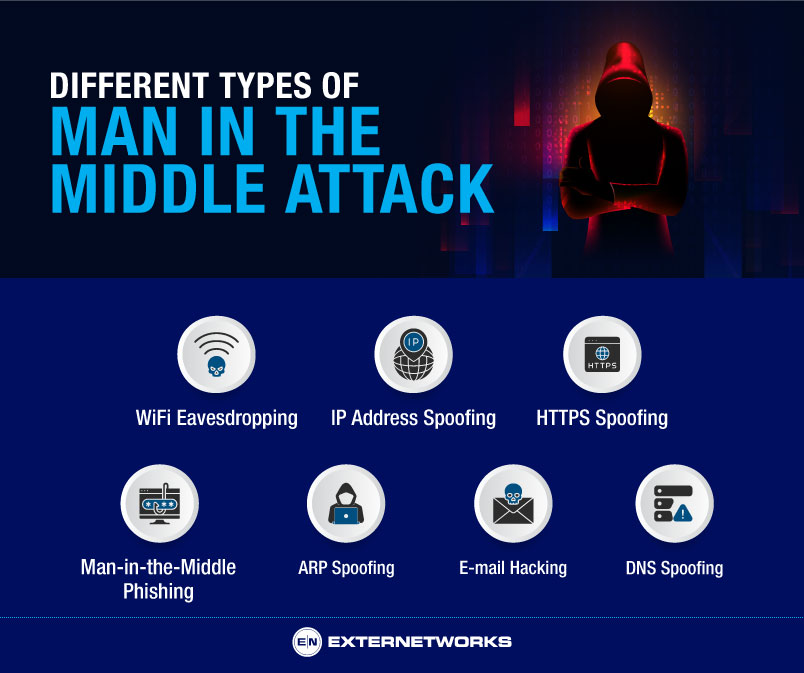
This type of attack occurs when the hacker targets a user or organization’s traffic to gain access to data that can then be used for malicious activity. The attacker does this by inserting themselves between the two points of communication, allowing them to intercept, control, and modify data as it passes through.
These attacks are especially successful on sites that require secure authentication with a public key and a private key, like online banking and e-commerce sites, as these give attackers easy access to users’ login credentials and other confidential information.
The attack is usually carried out in two steps: data interception and decryption. In this first step the attacker will find a way to intercept data between the client (user’s browser) and server (web site).
Hackers use several deceptive tactics in order to maintain control over intercepted communications such as IP address spoofing, DNS cache poisoning, or ARP spoofing. The next step is decrypting any encrypted messages that have been intercepted in order to gain access even more sensitive information from the transmitted context.
An outside party can launch a MITM attack through various methods, all involving intercepting victims’ information and activity. In some cases, hackers may need to unencrypt the data to make it readable and usable due to modern security protocols.
Imagine you’re in a Starbucks coffee shop and want free Wi-Fi. You see “STRBUX Free Wi-Fi” and connect your laptop. However, a nearby hacker is now watching your online activities without your knowledge.
The hacker established a deceptive Wi-Fi network to deceive individuals into utilizing it. In the meantime, the hacker can record passwords, usernames, and any confidential information that users input while connected to their network. Due to the lack of security and encryption, there is no need for decryption.
IP spoofing is a technique used by malicious actors to gain access to networks. With this attack, the attacker mimics an approved console’s IP address making it appear as if the system is legitimate. Therefore, they can stay hidden and track activities that may lead to unauthorized exploitation of the network. Depending on the situation, the attacker may launch a Denial of Service (DoS) attack to shut down the network or force unprotected systems offline.
To defend against such attacks effectively, organizations can benefit from Managed DDoS Services. These services provide proactive monitoring, detection, and mitigation of DDoS attacks, including those initiated through IP spoofing.
HTTPS spoofing is a sophisticated technique used by cybercriminals to bypass an encrypted communication system, such as a secure online banking structure. It is almost impossible to duplicate an HTTPS webpage, but fortunately, there are methods that can be used to deter this malicious activity.
In general, attackers create what is known as an authoritative address and use letters from international alphabets rather than the standard scripts found in phishing emails with unusual characters like Rólex instead of Rolex. This authoritative address theoretically allows for the attacker to evade detection by security systems.
In this type of attack, hackers create deceptive websites that mimic legitimate ones with the intention of obtaining victims’ confidential information. For instance, they may establish a website that resembles your bank’s site and request your login credentials. Once obtained, they can exploit this information to gain unauthorized access to your accounts.
ARP spoofing is a type of cyber attack that plays on the weaknesses in the Address Resolution Protocol (ARP) protocol. The attacker takes advantage of the fact that computers on a Local Area Network (LAN) use ARP to send requests for an IP address and generate responses containing both the MAC address and IP associated with it.
The attacker sends out a fake response, typically in place of the one from another computer on the same network. Thus, when devices check their ARP cache they see the unfamiliar MAC address and accept this as valid, while traffic directed to its original destination is intercepted by the malicious attacker instead.
Email hacking, also known as Email Hijacking, is a type of MiTM attack. In this attack, the hacker sends malicious emails to victims. These emails contain malware or phishing links. The intention is to deceive users into clicking on the links.
By doing this, the hacker can gain access to the victims’ accounts or devices. Email addresses can also be exploited for identity theft and other fraudulent activities. To protect yourself, it is advisable to always use a secure password for your email account and avoid clicking on any suspicious links.
DNS Spoofing is when an attacker creates a fraudulent web server to redirect a domain name to an IP address different than the one intended. This practice is effective because nearly all websites operate with numeric IP addresses, like 192.156.65.118, which is one of Google’s addresses.
For these sites to be interpreted into recognizable titles (such as google.com), DNS servers are used to translate the numeric code into the domain name that people know and can recognize easily. When DNS spoofing is done, users are unknowingly redirected away from their intended destination by attackers disguising their fraudulent web server as another known site.
Users may end up visiting malicious sites set up by hackers to download malware onto their devices or have essential information stolen, such as passwords and credit card information while believing they are still accessing legitimate websites due to the clever and convincing disguise employed by attackers via DNS spoofing techniques.
Network monitoring solutions can be used to detect suspicious activity and alert users or administrators when a possible MITM attack is underway. Additionally, virtual private networks (VPNs) offer secure communication tunnels that protect data from being intercepted by malicious actors.
Finally, they should consider implementing Multi-Factor Authentication to provide an extra layer of security for their users.
The security of mobile applications and Internet of Things (IoT) devices is increasingly becoming a concern as devices become more complex. Due to the lack of public awareness around the security measures that need to be taken with these types of devices, they often rely on protocols such as Telnet or HTTP that do not use encryption to communicate information.
This makes them vulnerable to attack by an attacker who can interject themselves in between the device and server by using a wireless access point or by spoofing the communication protocol.
SSL/TLS provides confidentiality, integrity, and authentication to network traffic by ensuring digital certificates are only accepted from reputable sources.
Unfortunately, attackers can use fake digital certificates to impersonate legitimate servers in Man-in-the-middle attack. This attack technique consists of setting up two separate sessions using SSL/TLS protocols.
One session will imitate the server and use the fake digital certificate, while simultaneously, a second session is used as a client connected to the legitimate server. By having two SSL/TLS connections, the malicious actor is able to gain control over the data transmitted between both parties undetected.
It is important to follow good IT practices within your company. Educate employees about the risks associated with these attacks. Keep software updated with security patches to minimize vulnerabilities.
Enable two-factor authentication for added security. Restrict access to sensitive data to authorized personnel only. Implement proper network segmentation to prevent unauthorized access. Ensure users not using weak passwords for all systems and avoid reusing them to enhance security.
Practicing good password hygiene by not reusing passwords across different accounts. A password manager should be utilized to generate strong passwords.
Advanced threat detection solutions can assist in achieving this objective, such as regularly scanning devices connected to the company’s network for vulnerabilities, automatically patching detected vulnerabilities, monitoring user activity within corporate networks, or conducting simulation tests using malicious software. There are multiple measures that companies can employ.
Man-in-the-middle (MIT) attacks are a prevalent technique utilized by cybercriminals to intercept and gain unauthorized access to encrypted content. These attacks exploit weaknesses in online communications systems to compromise the security of encrypted data.
Attackers frequently use various methods in Man-in-the-middle attacks to bypass encryption and gain unauthorized access to sensitive information. One standard method is session hijacking, where the attacker intercept and gains control of an ongoing communication session. This allows the attacker to listen to or manipulate the encrypted content.
IP spoofing is another technique used in MITM attacks, where the attacker impersonates a trusted IP address to intercept and manipulate the communication exchange.
These attacks undermine the security of encrypted communications by exploiting vulnerabilities in the communication stream.
MITM attacks have the potential to disrupt internet access and compromise communication integrity. These attacks are especially effective on public Wi-Fi networks, as attackers can easily intercept network traffic.
Transport Layer Security 1.3, a significant advancement in encryption technology, improves security by eliminating outdated encryption protocols and introducing more robust encryption algorithms. Additionally, TLS 1.3 enhances protection against MITM attacks through secure communication protocols and device/server authentication.
Conclusion
Man-in-the-middle attack are a serious threat to the security of encrypted data. Companies should employ various measures to prevent such attacks, including educating employees about good IT practices, implementing two-factor authentication and password managers, and utilizing advanced threat detection solutions. Additionally, TLS 1.3 provides enhanced protection against MITM attacks due its improved encryption algorithms and secure communication protocols.
