28.4k views
PCAP stands for packet capture. It’s used in many different ways, but one common use case is analyzing traffic between two hosts or servers. To understand how to use PCAPs effectively, we must know what they are and why they are helpful.
Packets are the smallest units of information sent across networks. A single packet contains one piece of data—such as an IP address, TCP port number, or HTTP request header—that travels over multiple physical connections. Each packet typically takes up less than a kilobyte of memory, making it easy to store and transmit.
A packet capture tool allows you to monitor and record packets as they travel across a computer network. This lets you see what’s happening behind the scenes of your organization’s network infrastructure. You could even use a packet capture tool on your home network to analyze bandwidth.
The most basic form of packet capture involves running software on a device that monitors network traffic and saves captured packets into a file. These files are called “packet captures.” They’re usually stored in the .pcap file extension.
You can find packet capture files on many devices, including routers, switches, firewalls, wireless access points, and computers. Some packet capture products let you view live network traffic, while others allow you to save captured packets for later viewing.
Captured packets can reveal a lot about your network traffic. In some cases, you can tell whether someone accessed a particular webpage by looking at the packets that traveled between your web browser and the server hosting that webpage. If you suspect that malware is attacking your system, you can look at captured packets to determine where that malware came from and what it did once inside your network.
In addition to analyzing network traffic, packet captures can be useful during a security incident investigation. After a data breach or other attack, investigators often want to know which hosts and ports were involved. By examining packets, they can identify each packet’s source and destination addresses, which helps them narrow down the scope of their investigation.
There are many different uses for packet captures. Here are just a few:
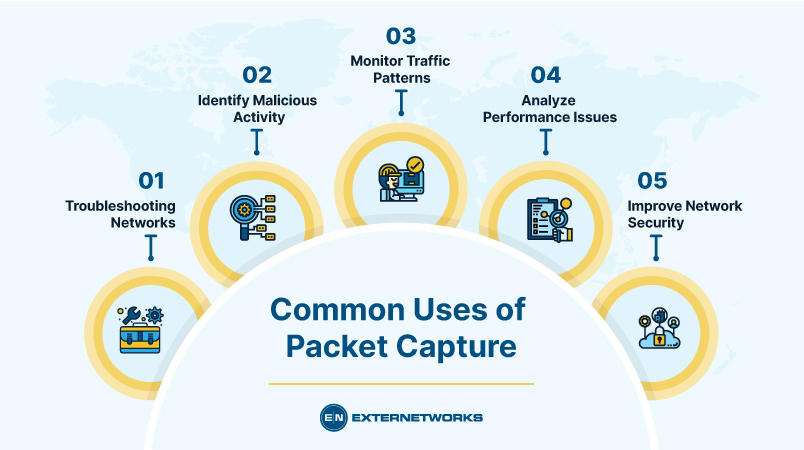
Troubleshooting Networks – Network problems can often be challenging to diagnose, and using packet captures makes troubleshooting much easier and allows you to see exactly which device is causing the problem.
Identify Malicious Activity – Malware like viruses and worms can cause significant damage to your system. By using packet captures, you can identify malicious activity on your network.
Monitor Traffic Patterns – Traffic patterns can tell you a lot about how people interact with your network. Using packet captures, you can easily track user behavior and find ways to improve your services.
Analyze Performance Issues – Sometimes, even though everything looks fine, your network isn’t performing well. Using packet captures will allow you to pinpoint the issue.
Improve Network Security – One of the most important things you can do to protect your network is to make sure that only authorized users are allowed to access it. Using packet captures lets you quickly identify unauthorized users.
PCAP is a powerful tool that allows you to monitor and control your network traffic. It can be used as an intrusion detection system (IDS) or to monitor your computer systems’ security. The following are some benefits of using PCAP:
In conclusion, Packet Capture is a powerful tool that allows you to see what is happening on your network. It gives you visibility into all the devices connected to your network and lets you see exactly where those devices are located. This makes it easy to troubleshoot issues and keep your network running smoothly.
