28.4k views
Have you ever wondered how hackers can gain unauthorized access to a website’s database and steal sensitive information? One of the most common techniques used by cybercriminals is known as a SQL injection attack.
In today’s digital age, where data breaches are becoming increasingly common, it is crucial to understand the various methods hackers employ to exploit vulnerabilities in web applications. SQL injection attacks have been a favorite among hackers for years, and they continue to be a significant threat to online security.
In this article, we will delve into the world of SQL injection attacks, exploring what they are, how they work, and the devastating consequences they can have on individuals and organizations. By understanding this malicious technique, you can proactively protect your website and valuable data from these cyber attacks.
SQL injection (SQLi) is a security vulnerability that enables attackers to manipulate SQL code within a web application’s database query, leading to potential consequences for both the application and the underlying database.
The SQL injection vulnerability allows attackers to inject code into SQL queries, giving them unauthorized access to and control over a website’s database.
Attackers can exploit SQL injection by inserting malicious code into input fields or parameters used in dynamic SQL statements, which may result in unauthorized access to the application or database.
Attackers can gain unauthorized access to sensitive information such as user credentials, personal data, or financial details. They can also execute malicious commands, such as modifying or deleting data stored in the database. Web applications are particularly vulnerable to SQL injection attacks if they do not properly validate and sanitize user input.
A successful SQL Injection Attack is performed by malicious individuals who exploit vulnerabilities in user inputs to gain unauthorized access to a web application or website’s database. The motivations behind such attacks can vary, but the primary goal is to bypass security measures and extract sensitive information or manipulate the database.
Vulnerable user inputs, such as login forms or search fields, are prime targets for attackers. These inputs are directly incorporated into SQL queries without proper validation or sanitization. The attacker is able to insert a malicious payload, usually in the form of SQL commands, into the input field.
When the application executes the SQL query, it interprets the injected code as valid SQL statements, resulting in unauthorized access to the database. This can have several consequences, including impersonation, data alteration, and database deletion. When the application executes the SQL query, it interprets the injected code as legitimate SQL statements, granting the attacker access to the database.
This can lead to various consequences, including impersonation, where the attacker gains the privileges of other users. Data alteration, where the attacker modifies or deletes data stored in the database, and even database deletion, where the entire database can be erased.
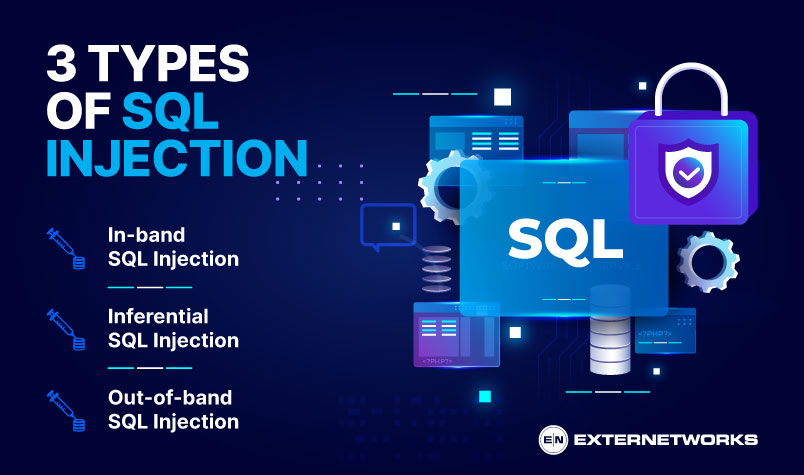
There are three main types of injection attacks: in-band SQL injection, inferential SQL injection, and out-of-band SQL injection.
In-band SQL Injection: This type of SQL injection attack is commonly observed. In this scenario, the attacker utilizes the same communication channel for initiating the attack and obtaining the outcomes. The attacker’s malicious SQL statements are executed on the database server, and the outcomes are then provided to the attacker.
Inferential SQL Injection: This type of attack, known as blind SQL injection, does not enable the attacker to directly retrieve the results of their queries. Instead, the attacker exploits loopholes in the application’s error messages or response times to infer the necessary information. For example, the attacker might send SQL queries that provoke different error messages for true and false conditions, allowing them to deduce information about the database.
Out-of-band SQL Injection: This type of attack differs from the previous two as it does not depend on the same communication channel. The attacker inserts SQL statements that initiate actions outside of the application’s environment, such as transmitting an HTTP request to a separate server controlled by the attacker. This can be advantageous in situations where direct communication with the attacker’s server is limited, but outbound connections are still permitted.
One of the most effective ways is to use prepared statements or parameterized queries, which separate the SQL code from the user input, making it impossible for attackers to inject malicious code into the SQL query.
This involves carefully checking and filtering input data to remove any malicious or unwanted characters. Input validation is recommended to be implemented on both the client side, using client-side scripting, and on the server side, by applying server-side validation rules.
Database administrators should ensure that users or accounts only have the necessary privileges to perform their tasks. This prevents attackers from executing malicious commands or gaining root access to the database.
Database vendors often release security patches and updates to address any identified vulnerabilities, and it is essential to install them promptly.
SQL injection prevention, businesses should consider implementing fundamental principles for defending websites and web applications. These principles include staff training to create awareness of SQLi-based risks and providing role-based training to all users. It is also important to keep user input in check, as any user input used in an SQL query can introduce risk.
SQL injection attacks have been a pervasive threat to web applications for many years and yet remain one of the most critical security risks. It is no surprise that at the top of the OWASP (Open Web Application Security Project), Top 10 list lies SQL injection, due to its ability to compromise confidential data from an application’s databases.
When successful, these attacks can have disastrous consequences; attackers are able to read, modify, recover, or execute malicious commands on the database. If a malicious query is entered into an application’s input field and is then executed exactly as written by the application in its backend database, a successful attack has occurred.
It is evident that SQL injection application vulnerabilities should not be taken lightly as they can easily cause much damage. Therefore, safeguarding against such attacks requires appropriate security measures like input parameter validation checks and parameterized query usage. Additionally, authentication and authorization mechanisms should also be used whenever possible so that unauthorized users cannot access sensitive information from within an application’s databases.
Web applications often load cookies and use their data as part of database operations.
Web applications commonly store data in cookies that are transmitted and stored in the user’s browser. This data can encompass session IDs, user preferences, or other pertinent information about the user. In the event that this cookie data is utilized as a component of a web application’s database operations, it can potentially create an opening for attackers in executing SQL injection attacks.
SQL injection attacks involve maliciously crafted SQL code that is embedded in the web application’s input. This code can be used to modify the database operations and extract sensitive information from the database. To protect against this type of attack, web application developers must ensure that all user-supplied data is properly sanitized before it is used in a database query. Additionally, they should regularly audit their code for potential vulnerabilities and patch them promptly.
A blacklist requires discovering every single character that can be malicious and will require retuning the blacklist as other security issues are identified and even as new exploits and exploit techniques are discovered. Confidentiality is often compromised with SQL Injection vulnerabilities as SQL databases typically store sensitive data.
SQL injection attacks have been a persistent and damaging threat to organizations across various industries. Examples of real-life SQL injection attacks that have caused significant damage to the affected organizations regarding financial loss and reputational damage.
Here are some real-life examples that showcase the potential dangers of these attacks:
Example 1:
Using SQLi to Authenticate as Administrator
In one of the most famous SQL injection attacks, an attacker was able to authenticate as an administrator of an organization by exploiting a vulnerability in the login page. The attack was successful due to the fact that the application’s input validation mechanism was not properly configured and allowed for bypassing authentication checks.
Example 2:
Using SQLi to Access Sensitive Data
In this attack, an attacker was able to access confidential information such as customer credit card numbers, addresses and phone numbers by exploiting a vulnerability in the application’s login page. The attack was successful due to the fact that the application did not properly validate user input and allowed for the injection of malicious SQL code.
Example 3:
Injecting Malicious Statements into Form Field
In this attack, an attacker was able to inject a malicious statement into a form field and gain access to the database. The attack was successful due to the fact that the application had inadequate input validation methods and exposed weaknesses in its security system.
These real-life examples underscore the significance of implementing robust security measures, such as input validation, using prepared statements, and regularly updating and patching systems to protect against SQL injection attacks. Organizations must be proactive in identifying and addressing potential vulnerabilities to safeguard crucial data and maintain the trust of their customers.
Implementing robust security measures, such as input validation, using prepared statements, and regularly updating and patching systems, is crucial in protecting against SQL injection attacks. It is important for organizations to be proactive in identifying and addressing potential vulnerabilities to ensure the safety of crucial data and maintain customer trust.
The exploitation of SQL injection occurs during the communication between web servers and database servers. Web applications interact with database servers to retrieve and store data. They often construct SQL statements dynamically, using user input to create database queries.
One method is SQL injection, which uses malicious SQL commands to modify the backend code and affect the Confidentiality, Integrity, and Authenticity of the data in the database.
For example, consider a student record application that allows users to search for student information by entering their ID using SELECT statements. The application constructs a SQL query based on the user input, like this:
“SELECT * FROM students WHERE id='” + userInput + “‘;”
In a SQL injection attack, an attacker can exploit this vulnerability by entering a malicious input such as “‘; DROP TABLE students; –” into the ID field. The resulting SQL query becomes:
“SELECT * FROM students WHERE id=”; DROP TABLE students; –‘;”
When this manipulated query reaches the database server, it is executed without proper validation. As a result, the attacker can execute arbitrary SQL commands, in this case, dropping the entire “students” table.
To mitigate the risk of SQL injection attacks, developers should implement strong security measures like input validation, input sanitization, and using prepared statements or parameterized queries. Regular security audits and patches are also crucial to maintain the integrity and security of web and database servers.
Conclusion
SQL injection attacks pose a significant threat to web applications and the sensitive data they handle. This type of attack exploits vulnerabilities in the application’s handling of user input, allowing attackers to inject malicious SQL statements into the database query.
Security researchers should also conduct regular audits and vulnerability assessments to identify any potential injection vulnerabilities and patch them promptly.
In the face of evolving cyber threats, businesses must prioritize protecting their data-driven applications. By understanding the risks posed by SQL injection attacks and implementing robust security measures, organizations can safeguard their sensitive data and maintain the trust of their users.
