28.4k views
Application security has become a major concern for businesses around the world. You need to invest in application security solutions to stay ahead of the game. If you want to know more about Application Security, read the article below.
Application security ensures that applications are safe from hackers and other malicious attacks. Application security aims to prevent attackers from accessing sensitive data or disrupting business operations.
Applications can be attacked in two ways: through a direct attack on the code itself (e.g., buffer overflows) or indirect attacks such as social engineering, phishing, and malware.
A hacker may use many tools to compromise an application, including exploits, backdoors, keyloggers, Trojans, viruses, worms, and denial-of-service attacks.
Application security is important because hackers use software vulnerabilities to steal computer information. Hackers also use malware to infect computers with viruses and spyware, which may cause damage to data, slow down computer performance, and expose users to identity theft.
The best defense against these attacks is to ensure that all software is updated and patched as soon as new versions become available.
In addition, web servers should only allow connections from trusted sources, and web browsers should only load web pages from known and trustworthy sites. Finally, users should never click on suspicious links or open unexpected file types.
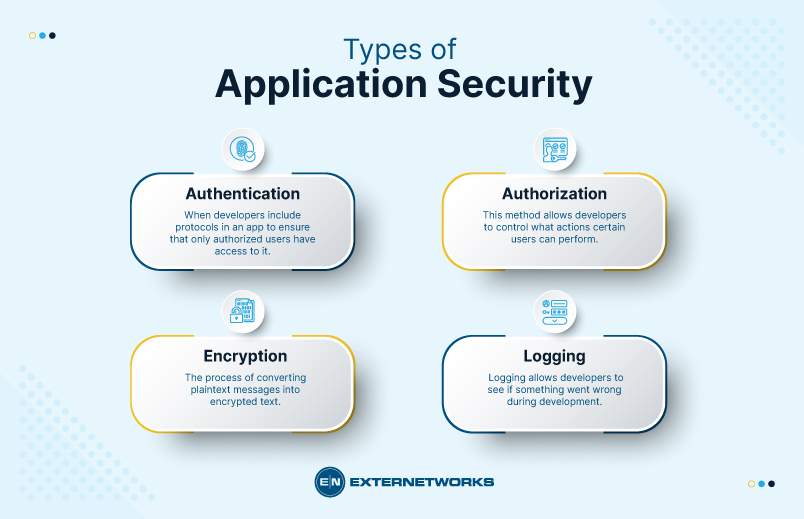
Application security encompasses many software protection techniques used to protect against attacks. In addition to authentication, authorization, encryption, and logging, several other ways to secure applications exist. These methods help prevent unauthorized people from accessing sensitive information.
When developers include protocols in an app to ensure that only authorized users have access to it. This type of security protects data stored within the application. The request fails if someone tries to gain access to the data without being properly authenticated.
This method allows developers to control what actions certain users can perform. For example, you might want to allow users to view some records but not edit others. Authorization helps keep track of who is allowed to do what.
The process of converting plaintext messages into encrypted text. Encrypting data prevents anyone else from reading it. The most common form of encryption is public key cryptography.
Logs record events so they can be reviewed later. Logging allows developers to see if something went wrong during development. It also helps identify problems after release.
Application security works by identifying potential threats and preventing them from reaching end users. For example, if a hacker were to try to log into a bank account using stolen credentials, the application would detect this attempt and prevent the user from being able to complete the transaction.
To protect against these kinds of attacks, applications need to identify and block any attempts at the unauthorized activity. To accomplish this, they typically rely on two main methods:
To identify the source of an attack, applications check each incoming request against a list of known good requests. If the request matches a bad request, the application stops the attack. In addition, the application might record the IP address of the client requesting so that it can be reported later.
To prevent an attack, applications perform checks and determine whether a particular action is allowed. The most common form of prevention involves checking the validity of client input parameters. If a parameter is invalid, the application returns an error message instead of performing the requested operation.
Prevention occurs when the application automatically performs actions based on its knowledge of handling situations. You added a product to your shopping cart but haven’t paid for it. Your browser requests the server to confirm that you will not pay for it. The application detects this situation and cancels the order before committing to buying the product.
Preventing these attacks requires developers to anticipate every possible scenario and write code to deal with them. There’s no way to know which scenarios will occur. Many applications use heuristics to predict the likelihood of various attacks.
Application Security Risks are of 3 types:
A vulnerability is a weakness or flaw in the design of an application that allows attackers to compromise the system. A vulnerability could take several forms, including buffer overflows, SQL injection, cross-site scripting, etc. Vulnerability management is one of the most important aspects of securing an application because vulnerabilities can lead to malicious activities such as stealing confidential information, defacing websites, or launching denial-of-service attacks.
Malicious activities include violating the website’s terms of service, such as posting inappropriate content or accessing sensitive information without authorization. They also include actions taken by third parties who gain access to the site through the attacker’s exploit gain access to the site through an exploit in the application. For example, if an attacker gains control over a user’s session cookie, she may be able to view other users’ personal information. Or if an attacker manages to bypass authentication controls and log in as another user, he may be able to change his profile or cause damage to the site.
Privacy violations involve violating the privacy of individuals using the application. Examples include obtaining personally identifiable information (PII) about users without their consent, collecting PII without permission, or sharing PII outside the organization.
Application security is a subset of network security since both terms called privacy violation involve another term involving collecting or using personally identifiable information (PII) without permission. PII includes information that identifies an individual, such as name, social security number, date of birth, mother’s maiden name, home address, telephone number, and so on. PII includes credit card numbers, bank account numbers, Social Security numbers, medical records, etc.
In conclusion, application security is essential to network security because it helps prevent unauthorized access to systems and networks. Finally, application security plays a key role in protecting against cybercrime. Keeping your company’s applications secure can reduce the risk of identity theft, financial loss, and legal liability.
