28.4k views
Have you ever heard of a brute force attack? It’s a type of cyber attack that can be used to gain unauthorised access to sensitive information. But what exactly is it, and how does it work?
As technology advances, so do the methods cybercriminals use to steal data. A brute force attack is one such method that has existed for a long time. It involves trying every possible combination of characters to crack a password or encryption key.
In this article, we’ll look at a brute force attack, how it works, and how to protect yourself. Understanding this type of cyber attack is crucial in today’s digital age, where data breaches have become common. So, let’s dive in and learn more about this threat to our online security.
A brute force attack is a malicious cyber technique to access credentials and confidential information. Hackers employ this tactic by trying out every possible combination of letters, numbers, symbols, and other characters to crack the code or confirmation key.
This trial-and-error method of guessing login information can be very effective and time-consuming since it covers all the potential combinations. Depending on the length and complexity of the password, cracking it can take anywhere from a few seconds to many years. It’s an unsophisticated yet effective way for hackers to penetrate private networks, websites, and databases if they have enough computing power or a botnet.
Brute force attacks are not new—hackers have been using this strategy as far back as computers have existed—but they remain popular today. After all, sometimes, the most straightforward tactics can result in successful breaches. An example would be when a hacker uses extensive data mining techniques coupled with dictionary files filled with common words such as “P@ssw0rd!” in hopes of discovering user passwords; this is known as a dictionary/wordlist attack. The goal here is always to gain unauthorized access to systems intended only for users.
Brute force attacks can be used against any type of authentication system, such as websites, applications, databases, and even networks. When an attacker launches a brute force attack, they generally start by running automated scripts to generate random username and password combinations. These combinations can range from simple words or phrases to complex strings of characters.
Once the attack is underway, the attacker will continually attempt to log into the system using these generated combinations until they find a valid username and password combination. Because brute force attacks are automated, they can be challenging to stop as the attacker has no limit on how many attempts they can make. As such, it is vital to employ security measures to detect and block brute force attacks before they become successful.
For example, if an attacker targets an account with a four-letter password composed only of lowercase letters, they would use a program to test all possible combinations starting from “aaaa” until “zzz”. The possibilities become significantly fewer when dealing with more complex passwords that include numbers and symbols; however, brute force attacks drastically reduce the time needed for a hacker to attempt numerous options to gain access, making them extremely effective at what they do regardless of encryption strength.
Brute force attacks are notoriously difficult to prevent since they take advantage of a computer’s ability to repeat many repetitive tasks quickly and easily. Typically, Brute force attacks can be divided into five main types, each designed to increase the chances of a successful login. These include Simple Brute Force Attacks, Dictionary Attacks, Hybrid Brute Force Attacks, Reverse Brute Force Attacks, and Credential Stuffing.
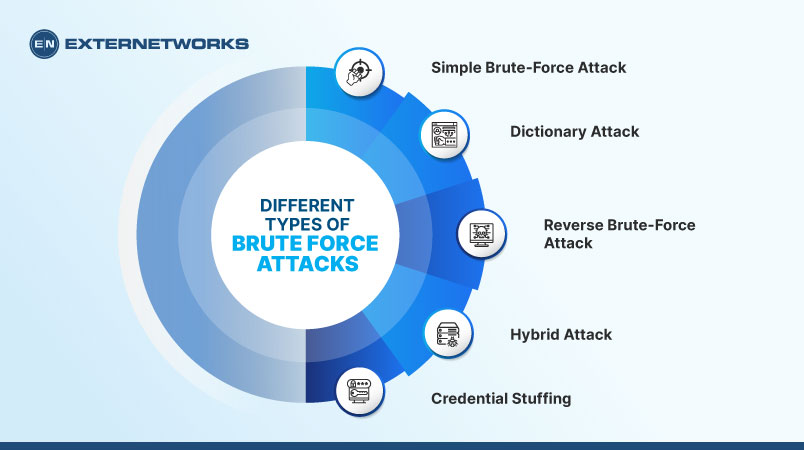
A simple brute-force attack involves rapidly trying every possible combination of letters, numbers, and symbols to crack a password. Attackers can use software to automate this process, which makes it easier and faster.
A dictionary attack involves using a list of potential passwords to guess the correct one. Attackers can use a pre-built dictionary with common passwords, such as “password” or “123456”. They can customize the dictionary to include relevant terms specific to the target victim.
In a reverse brute-force attack, the attacker knows the password they want to use and attempts to identify the corresponding username. They can try the password with different usernames until they get the correct one. This method can be effective when the attacker has limited information on the target.
A hybrid attack combines brute-force and dictionary attack methods. The attacker will use a dictionary attack first but modify the words with memorable characters, numbers, or capitalization, then perform a brute-force attack on the changed passwords. This method can crack relatively complex passwords.
This attack uses stolen credentials from other websites or databases that have been compromised and then tries them against the target website or system.
Brute-force attacks are becoming increasingly common in the digital age. Organizations need to safeguard their systems against this type of cybersecurity attack. The best way to protect against brute-force attacks is by implementing a layered approach that includes increasing password complexity, enforcing password manager rules, limiting failed login attempts, and encrypting data using 256-bit encryption and password hashes.
Increasing the complexity of passwords makes them difficult to crack, reducing the time required to decrypt them. Organizations should also enforce strict password manager rules, like a minimum passphrase length or compulsorily enabling special characters during login.
Limiting failed login attempts further helps protect networks by locking users out after repeated attempts have been made. Finally, encrypting and hashing data with 256-bit encryption exponentially increase the computing power required for a brute-force attack, adding an extra layer of security protection. By combining all these different layers of protection against brute-force attacks, organizations can significantly strengthen their cybersecurity posture.
In today’s digital age, maintaining strong passwords is crucial to protect one’s online security. With increased cyber-attacks, data breaches, and identity theft, it’s essential to create strong passwords that cannot be easily guessed or hacked. Below are some tips for creating strong passwords:
Use a mix of characters: A strong password should contain a combination of uppercase and lowercase letters, numbers, and symbols. This mix of characters makes it harder for hackers to guess or crack passwords. Using special characters such as hashtags or dollar signs can also add a layer of protection to the password.
Avoid common words: Hackers use automated tools to easily guess simple passwords. Avoid using common words like “password,” “123456,” or “qwerty,” as they are the most commonly used passwords. Instead, use random combinations of characters that make no sense together. This practice makes your password much harder to crack.
Don’t use personal information: Avoid using any personal information like your name, birth date, or phone number in your password. Hackers can easily find this information through social media or other online platforms and use it to guess your password.
Use a passphrase: A passphrase is a group of words that create a longer and stronger password. Create a unique phrase that only you know and have not used before. Using a phrase instead of a single word makes it more difficult for hackers to guess or crack.
Use two-factor authentication: Two-factor authentication provides an additional layer of security to your password. Accessing your account and your password requires a second form of identification. This form of authentication significantly reduces the risk of unauthorised access to your account.
Conclusion:
Prevention is key when it comes to thwarting brute force attacks. To protect against these malicious attempts to gain access, organisations should implement a layered approach that includes solid and unique passwords, password manager rules, limiting failed login attempts, and encrypting data with 256-bit encryption and password hashes.
Organizations can significantly reduce the risk of a brute force attack successfully accessing their systems by taking such measures. Additionally, organizations must provide employees with adequate training on cybersecurity best practices to ensure they understand the importance of strong online security measures.
At ExterNetworks, we understand the importance of staying one step ahead in the ever-evolving landscape of cyber threats. With our proactive monitoring services, you can rest easy knowing that potential threats are being identified and addressed before they can impact your organization. Our team of cybersecurity experts brings years of experience to the table, ensuring that your systems are always protected against the latest threats.
We offer customized solutions to fit your unique cybersecurity needs, ensuring you receive the level of protection your organization requires. Additionally, we help keep your organization compliant with industry regulations and standards, giving you peace of mind knowing that your data is secure.
By choosing ExterNetworks for cyber threat monitoring services, you can save on the costs of hiring an in-house security team while benefiting from top-notch protection. Don’t wait until it’s too late—contact ExterNetworks today to learn more about how our services can benefit your organization.
