28.4k views
Security is crucial in the digital age. Are you confident in your online account and personal information security? Relying on passwords alone can leave you vulnerable to cyber attacks. This is where multi-factor authentication (MFA) comes in.
Due to the rising number of data breaches and hacking incidents, it is important to implement additional security measures to safeguard our sensitive information. Multi-factor authentication is a method that adds an additional layer of protection by mandating multiple forms of verification before granting access to an account or system.
Multi-factor authentication, or MFA, is an important tool for protecting against unauthorized access and identity theft. By using a combination of factors like passwords, mobile devices, and biometrics, MFA greatly enhances the security of your online accounts.
This article will discuss the significance of MFA and address common misconceptions that may hinder the adoption of this effective security measure.
Multi-Factor Authentication (MFA), also known as Two-Factor Authentication (2FA), is an authentication method that enhances security during the login process by requiring users to provide multiple verification factors. This helps to minimize the potential for unauthorized access to sensitive information or systems.
Common authentication factors used in MFA include one-time passwords generated by authenticator apps or sent via SMS, smart cards that are physically inserted into a reader, facial recognition, or personal security questions. These additional factors enhance the security of the authentication process, making it more challenging for unauthorized individuals to gain access.
It provides an additional layer of security for user identities and corporate networks, ensuring that only authorized individuals have access to valuable information or systems. MFA has become a foundational component of many organizations’ identity and access management strategies.
MFA authentication method requires users to provide additional authentication factors beyond just a username and password.
The traditional method of using only usernames and passwords is vulnerable to various cyber attacks, such as phishing attacks or brute-force attempts. Cybercriminals can easily steal or crack login credentials, gaining unauthorized access to sensitive information.
MFA mitigates these risks by adding an extra layer of security. By requiring additional authentication factors, such as something the user knows (password), something the user has (smart card or mobile device), or something the user is (biometric authentication), MFA significantly reduces the likelihood of unauthorized individuals gaining access.
Multi-factor authentication is classified into two categories:
MFA for devices: A two-factor authentication process that verifies a user at the point of login.
MFA for applications: A two-factor authentication process that verifies a user to allow access to one or more applications.
Both MFA functions in the same way. The process typically involves implementing multi-factor authentication in the user account and linking it to an MFA app or program. The user is then prompted to input the associated token for the account, which may be a random number generated by an app similar to Google Authenticator.
In order to compromise your account, the hacker must have access to the token. That is why MFA is a valuable tool for enhancing your IT security.
The three main types of MFA authentication methods are based on knowledge, possession, and inherence factors.
The knowledge factor is a component of MFA that requires the user to provide information they know, such as a password or PIN. It is the most commonly used factor in MFA and adds an additional level of security to the login process.
The possession factor requires the user to have something physical, such as a mobile device, smart card, or physical token. This factor ensures that the user has a physical object in their possession in order to complete the authentication process. It adds an additional layer of security by making it more difficult for unauthorized individuals to gain access to the user’s account or sensitive information.
The inherence factor is based on unique physical characteristics or biometrics of the user, such as fingerprint or facial recognition. This factor provides a highly secure form of authentication as it relies on something inherent to the user that is difficult to replicate or fake. By combining this factor with other authentication factors, MFA further enhances the security of the login process.
There are various checks available for implementing MFA, and the list is continually expanding. We have selected the common picks here.
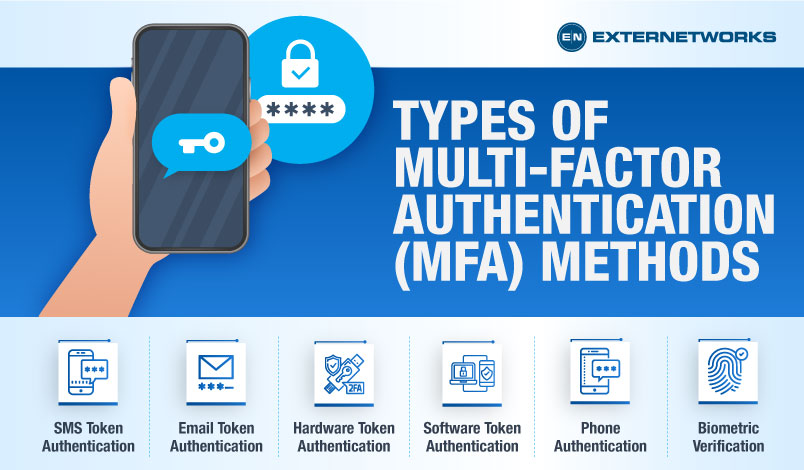
SMS token authentication is a commonly used security measure by organizations to safeguard customer’s confidential information. This method involves users receiving a unique, one-time PIN code via SMS or text message. This code is used alongside a username and password for verification to access sensitive data. By using an SMS token, users can have peace of mind knowing that their information is protected even if they lose or forget their login credentials.
In addition, offering this form of authentication on mobile devices is especially helpful since many people prefer to access services using mobile devices instead of having to use traditional desktop computers. As long as users can easily have access to SMS tokens on their mobile devices, then organizations can make it simpler and quicker for customers who want to securely login into their accounts without continually having to enter additional passwords over again while still keeping security measures intact.
Email token authentication is a commonly used two-factor authentication method that provides a secure and convenient way for users’ identities verification. This method involves sending a unique code or “token” via email, which users can use for account authentication. The code has a limited time window for validity, ensuring minimal risk of fraud or unauthorized access.
This method provides several advantages compared to other two-factor authentication methods like SMS tokens. Users can access their emails anytime, eliminating the need to have their phone nearby for the code to be received. This eliminates concerns about the physical device being lost or stolen.
Hardware token authentication is a security method that involves the use of physical hardware devices to access services. These devices are typically small USB-powered devices that need to be connected to a computer or mobile device for service usage. This type of authentication is commonly used by institutions like banks, investment firms, and secure sites that prioritize strong security measures.
By utilizing an authentication application on a mobile device, users can achieve a comparable level of security to that of a hardware token. Essentially, the smart device serves as the token and can be integrated with services such as Google Authenticator.
Encouraging customers to utilize a third-party solution can enhance the implementation of MFA for their other services, thereby enhancing their overall security. Additionally, it provides a convenient option for attaching a hardware token to a smart device, thereby eliminating the requirement for an extra dongle.
One common method of user authentication via phone is through randomly generated one-time passwords (OTPs) sent by SMS. Another method is through automated phone calls.
Individuals who possess a smart device or computer equipped with biometric authentication, such as fingerprint ID or facial recognition, can utilize this verification method to confirm their identity as part of MFA. Biometric ID verification is generally more convenient than inputting an OTP, resulting in customers finding it less bothersome to employ on a regular basis. The decreased difficulty makes it an optimal choice when additional checks are necessary.
Factors are pieces of information that a user can provide to verify their identity. The most commonly used form of authentication is 2FA, however, security professionals today utilize a total of five factors of authentication.
The knowledge factor plays a vital role in multi-factor authentication, an advanced method that enhances the security of systems and networks. This factor validates the identity of a user by requesting information that is exclusively known to them.
The knowledge factor encompasses anything a user can remember, type, say, do, execute, or otherwise recall when needed. It is an effective authentication method because it relies on information that is unique to each individual user, making it difficult for unauthorized users to impersonate or gain access.
Passwords, PIN codes, and security questions serve as knowledge elements in multi-factor authentication. By combining this knowledge factor with other authentication factors, organizations can implement a robust and secure authentication process that safeguards user identities, corporate networks, and sensitive data.
The possession factor encompasses various examples, including physical devices and digital assets. Physical devices, such as mobile phones, security tokens, and hardware fobs, can be used to generate one-time passwords or receive verification codes. These devices are uniquely possessed by the user and serve as a tangible means of verifying identity.
Digital assets, such as email accounts and authenticator applications, also fall under the possession factor. These assets are typically protected by passwords or other access control measures, ensuring that only the rightful owner can access them.
The inherence factor is another component of Multi-Factor Authentication (MFA) that verifies a user’s identity based on physical attributes unique to them. This authentication method leverages biometric technology to validate the user’s inherence factor, ensuring a higher level of security.
Biometrics involves the use of physical characteristics such as fingerprints, voice recognition, facial recognition, and behavioral biometrics to verify a user’s identity. Fingerprints are one of the most commonly used inherence factors in MFA. Each person has a unique fingerprint pattern, making it highly reliable for authentication purposes.
Voice recognition is another popular inherence factor that analyzes the unique vocal characteristics of an individual. This method of comparing the user’s voice against a pre-recorded sample ensures a high level of accuracy in verifying the user’s identity. It captures and analyzes these characteristics to authenticate the user.
This is based on the expectation that specific actions, like logging into a work computer, should occur within established time frames. If an access attempt occurs outside of the normal range, it may be questioned or stopped until the user can verify their identity.
Location factors of authentication are utilized to confirm the identity of a user by assessing their geographical location. For example, if a user registered their account in one country and there are login attempts from another, location factors may be activated to authenticate the identity of the new user. These factors typically involve comparing the IP addresses of the original user and the new attempt to access information.
Multifactor Authentication (MFA) and Two-Factor Authentication (2FA) are methods employed to enhance user authentication security, although they do have distinct differences.
Two-Factor Authentication (2FA) is a type of Multi-Factor Authentication (MFA). It requires two authentication factors to confirm a user’s identity. These factors usually involve something the user knows (such as a password) and something the user has (like a mobile device). For instance, when logging into an account with 2FA, the user would enter their password and then receive a temporary code on their mobile device. They must enter this code to complete the login.
Multi-Factor Authentication (MFA) provides more security options than just two factors and offers flexibility for enhancing security measures further. MFA includes additional authentication methods like biometrics (fingerprint or facial recognition) and hardware tokens (smart cards or physical devices). These extra factors greatly enhance authentication strength and decrease the risk of unauthorized access happening.
MFA enhances security by utilizing various authentication methods, providing an additional layer of protection against attackers attempting to compromise user identities. Additionally, organizations can tailor their authentication process to align with their unique security requirements and risk profile.
Artificial intelligence (AI) can play a crucial role in enhancing multi-factor authentication (MFA) by analyzing user behavior and identifying suspicious activity. Through the use of machine learning algorithms, AI can analyze trends and patterns in user activities, allowing for a more accurate assessment of the authenticity of login attempts.
By monitoring user activity, AI can establish a baseline of normal behavior for each individual user. This baseline can encompass factors such as login times, locations, and device usage patterns. Any deviation from this established baseline can be flagged as potentially suspicious, triggering additional authentication measures.
AI can assign risk scores to different login attempts based on various factors, including the user’s past behavior, the device being used, and the IP address. By evaluating multiple factors simultaneously, AI can determine the likelihood of unauthorized access more accurately.
Furthermore, AI can adapt and learn from ongoing data, continuously updating its algorithms to better identify new and evolving threats. This dynamic approach allows AI-powered MFA systems to constantly improve their accuracy and effectiveness, minimizing false positives while maximizing security.
Multi-factor authentication (MFA) is a security measure that is becoming more important. It adds an extra layer of protection against unauthorized access and data breaches. By using various authentication methods, such as biometrics, push notifications, one-time passwords, and hardware tokens,
MFA helps to safeguard user identities and sensitive systems from malicious individuals. Additionally, artificial intelligence (AI) can enhance the effectiveness of MFA by analyzing user behavior and assigning risk scores to different login attempts. To ensure the safety of their users and data, organizations should consider implementing MFA as part of their security measures.
