28.4k views
Have you ever heard of a rootkit? If you’re unfamiliar with the term, it’s important to learn about it as it can seriously threaten your computer’s security.
In cybersecurity, a rootkit is a type of malicious software that allows an attacker to gain access to and control your computer system. Hackers often use rootkits to steal sensitive information, such as passwords and financial data, or to use your computer as part of a larger botnet for further attacks.
Understanding what a rootkit is and how it works is crucial in protecting your computer and personal information. In this article, we’ll go over the basics of rootkits, how they can infect your computer, and what you can do to prevent and remove them.
A rootkit is a malicious program that gives a threat actor remote access to a computer or other system. Rootkits are used for nefarious purposes like installing viruses, ransomware, and keylogger programs. They can also be used to bypass standard security measures and control a system completely with admin privileges. As a result, rootkits are very dangerous tools and must be dealt with immediately if detected.
Rootkits have been around for quite some time, but older antivirus programs often struggle to detect them. Nowadays, antimalware programs are specifically designed to scan for and remove any lingering rootkits on a system. Furthermore, one can purchase dark web rootkits highlighting the importance of cybersecurity measures like user awareness training, multi-factor authentication, and self-monitoring accounts online for any suspicious activity.
Unlike some other forms of malware, rootkits cannot spread themselves through the Internet or email – they must be installed to become active on a target system. A typical rootkit is usually disguised as an innocuous program, and once it’s permitted to install itself on the victim’s computer, it sets about concealing its presence until its operator activates it.
Once activated, a rootkit can install additional malicious tools, such as banking credential stealers and password stealers, keyloggers, antivirus disablers, or bots for distributed denial-of-service attacks. While rootkits can get into computers through a variety of channels – from phishing emails with executable files attached, crafted PDFs or Word documents, and compromised shared drives to risky websites with infected software downloads – one thing remains constant: they give their operator’s relentless control over the affected machine without the user’s understanding or consent.
They are classified based on how they infect, operate, or persist in the target system. The most common types of rootkits include:
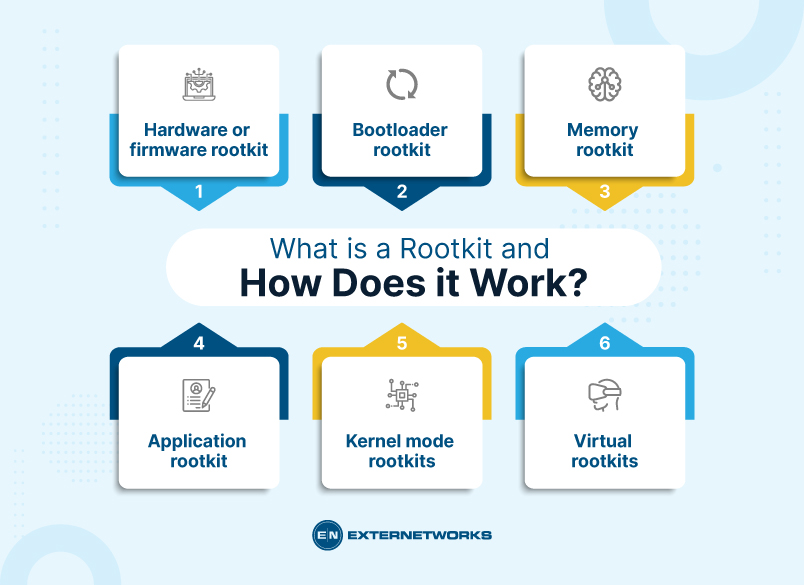
Hardware or firmware rootkits are malicious programs designed to infect a computing device at a low level and, in most cases, remain hidden while allowing the hacker to gain privileged access and control. These types of rootkit can penetrate your device’s hard drive, router or system BIOS – the software installed on a tiny memory chip usually located on the motherboard.
Rather than directly targeting an operating system, these particular variants use the various hardware components to install malware and spyware that are much harder to detect with conventional anti-virus solutions. If infiltrated through this method, malware could go undetected while it records keystrokes and monitors web use remotely, ultimately granting hackers remote control over their victim’s computer systems. While less frequent than other forms of rootkits, any possibility of inferal must be taken seriously due to the potential seriousness of the infection.
Bootloader rootkits are malicious software programs that infiltrate a computer’s bootloader mechanism, replacing the legitimate version with a malicious one. A bootloader is responsible for loading the operating system as soon as the computer starts. By replacing this component with its own malicious version, the perpetrator can control what is loaded at startup and gain access to your data without your knowledge.
Once active, bootloader rootkits remain active even before your computer finishes loading the operating system. This form of malware takes advantage of low-level system architecture by creating an interactive backdoor that grants the attacker unauthorized access to any parts of your system. It also allows them to monitor user activities, steal data, install additional malware, or even modify existing files on your hard drive without alerting you in any way.
Bootloader rootkits can be extremely difficult to detect and remove without proper protection since they operate in such an integral part of a system’s infrastructure. Unfortunately, these attacks have become increasingly common over recent years and can cause serious harm if left undetected.
Memory rootkits are malicious pieces of software that target your computer’s RAM. Unlike traditional rootkits that inject code into your system and remain active even after a reboot, memory rootkits quickly disappear when the system is restarted. Despite the short lifespan, memory rootkits can cause severe damage if left unchecked.
Because memory rootkits operate entirely in RAM, they have access to most of the parts of your system, including sensitive information such as passwords and credit card numbers. They also affect RAM performance by taking up valuable resources and impairing computer operation speed and stability. Furthermore, a security scan may not detect any malware infection since it doesn’t last long enough to be picked up. That’s why taking measures immediately at the first signs of a potential memory rootkit infection is important, such as crashing applications or malfunctioning hardware.
They infect popular applications, such as Microsoft Office, Notepad, and Paint, by replacing their standard files with rootkit files, allowing them to gain access whenever the programs are used. These malicious software applications can also change how these programs work without the user being aware. This makes application rootkits especially hard for users to detect since the infected programs often still operate normally – any abnormal behavior may go unnoticed by the user.
To prevent such attacks and stay safe online, it is important to use antivirus programs that are equipped with features that can specifically detect application rootkits. Most modern-day antivirus programs can search through operating system code at a very low level to scan and detect these malicious attacks before any damage can occur. This double-layer protection on both the application and operating system layers is a good preventive measure against most types of malware threats.
A Kernel mode rootkit is a type of malicious software that utilizes its access to the deepest level of an operating system, otherwise known as the kernel, to gain complete control of a device without the user’s knowledge. These rootkits effectively give hackers a back door entry point into an unsuspecting user’s computer and are some of the most severe threats against cyber security.
With complete control over the kernel and underlying functions, hackers can access information such as keystroke logs, data files, boot configuration settings, and confidential user credentials stored in memory. They can even modify code to remain invisible to antivirus software or replace existing system processes with their own applications.
This puts any personal or sensitive data stored on the computer at risk of being stolen, deleted, or altered somehow. Additionally, since these rootkits operate on a deeper level than standard antivirus programs are designed to detect, their presence can go unnoticed for extended periods while they cause chaos behind the scenes.
A virtual rootkit is a particularly malicious type of malicious software that can be installed on a computer system without any direct interaction with the user or detection by antivirus programs. It loads itself underneath the computer’s operating system, then hosts the target operating systems as a virtual machine. This allows it to intercept hardware calls made by the original operating system, enabling the hacker to gain access to private data or issue commands on behalf of the user. Virtual rootkits enable hackers to bypass system security checks and obscure their activity from other users and processes.
Virtual rootkits have been traditionally difficult to detect for antivirus software because they don’t require kernel modification to subvert the operating system, making them invisible compared to other malware variants. Some modern-day virtual rootkits are also designed with built-in cloaking mechanisms, making them very difficult for most malware scanners to identify. Nonetheless, users can still take certain measures, such as using reputable antiviruses and ensuring regular updates on all their machines to help mitigate against this type of attack.
Rootkit detection is a difficult problem, as there are relatively few effective mechanisms for detecting these malicious bits of code. So far, one of the most successful methods has been to look at strange behavior on a computer system. This means that anti-virus programs and similar security tools can attempt to notice any abnormal activities or files—if something looks off, it signals that something malicious could lurk under the surface.
Another method for rootkit detection involves signature scanning, where the anti-virus program examines all the files on your machine to see if it recognizes any known viruses or malware snippets. This allows for more precise identification but requires updates to be able to detect new threats quickly.
Memory dump analysis is a more advanced technique in which examining memory states can provide clues about what processes are running and their location in memory. Unfortunately, these techniques may not be enough depending on the type and sophistication of rootkits in question; in many cases, the only way to remove them is by completely wiping out the compromised system and starting over again from scratch.
Rootkits are a significant security problem of modern times, as they can penetrate computer systems without notice. Rootkits target the very core of a system’s operating system and hide malicious processes or files from users. It is important to be aware of rootkits and take steps to protect your system from them.
To prevent rootkits’ installation, ensure your system is always up-to-date with patches for known vulnerabilities in your OS, applications, and virus definitions. Furthermore, only download and install software from trustworthy sources and pay attention when installing them; read the end-user license agreement closely as it contains vital information about how an application works, what permissions it will require, etc.
Avoid opening email file attachments from unknown sources or those sent unexpectedly by people you know; these could easily contain malicious Trojans or viruses that may lead to installing a rootkit on your machine. Taking these precautions will ensure that you have a secure system and reduce the likelihood of becoming susceptible to rootkit attacks.
TDSS:
The TDSS rootkit is a form of malware that was first identified in 2008. It uses techniques similar to other bootloader rootkits, loading itself and running code while the operating system is still booting up. This makes detection of the infection incredibly difficult, as there isn’t much time for anti-malware software to work before full execution. Fortunately, this type of malware can often remain undetected in the wild due to its low-profile nature; however, it still continues to be a major security threat for those that possess outdated systems and lack sufficient protection.
The TDSS rootkit greatly impacted computer security when it was discovered. Security professionals struggled to find ways to detect and remove it as removal of the bootsector code requires editing of protected areas of the hard drive or reinstallation of the operating system. As a result, anti-virus companies had to create new protection approaches in order to combat this virus effectively, making anything loaded after OS initialization vulnerable to deep examination by scanning engines. In addition, they had to come up with methods for monitoring deeper areas within the system which may give early warnings against malicious attacks such as TDSS rootkits.
Flame:
Flame, a powerful rootkit used to carry out cyber espionage, was first uncovered in 2012. Since then, the full potency of this malicious software has been revealed. It reports back via 80 servers located across continents, giving the hackers behind Flame unprecedented access to infected computers. Flame can monitor traffic, take screenshots and audio recordings, and log keystrokes from any device.
This infiltrating malware can get to the deepest parts of an operating system, giving it unbridled control over its victims. Despite its devastating power and many attempts to reveal the identity of those responsible for its creation, those exact individuals remain mysterious. The far-reaching implications of this malevolent signature are still being discovered today, with companies around the globe have unknowingly fallen victim to it without realizing it until long after the invasion had occurred.
Necrus:
Necurs is one of the most prolific malware infections in the cyber security world. It was first detected in 2012, spreading like wildfire throughout numerous computer systems around the globe. In just that year alone, an estimated 83,000 infections were reported. This particular rootkit is associated with elite cybercriminals in Eastern Europe and has developed a reputation for its technical sophistication and adaptive capabilities. To this day, security experts have continued to monitor the infection it causes and look for new ways to mitigate its damage.
In addition to evading standard virus scans, Necurs features complex mechanisms that allow it to discreetly harvest private data from infected hosts without raising suspicion or alerting antivirus programs. With every new version released, its modus operandi becomes more sophisticated as attackers look for newer ways of seizing control over vulnerable computers. Although countless solutions have been proposed to combat it, Necurs remains a major threat for regular users and corporate networks worldwide.
ZeroAccess:
ZeroAccess is one of the most notorious rootkits of the early 2010s. First discovered by cybersecurity experts in 2011, this malicious code infiltrated over two million computers worldwide. Once installed on a machine, the rootkit repurposes it as part of a botnet used to launch coordinated cyberattacks on victims. This malware does not directly affect the infected computer’s operational capability; instead, it secretly downloads and installs additional malicious software that can be used to steal personal information such as passwords and credit card numbers.
Today, ZeroAccess remains an active threat to internet users worldwide. As long as cybersecurity practices stay stagnant and out-of-date, attackers using ZeroAccess will likely continue penetrating computer systems for their own gain. To defend yourself against this sophisticated attack, you should ensure that your anti-malware solution can identify and block advanced threats before they can do any real damage.
Conclusion
Rootkits are a form of malicious software that can evade detection and give attackers control over vulnerable systems. Over the years, some of the most dangerous rootkits have infiltrated millions of computers worldwide, exposing victims to cyber espionage and data theft. The TDSS, Flame, Necurs, and ZeroAccess rootkits are just a few examples of how powerful these infections can be.
With the widespread prevalence of rootkits, all computer users need to be aware of their presence and how to protect themselves against them. Network administrators should actively monitor their systems and deploy adequate security measures to prevent malicious software from entering them. It is also important for individual users to regularly update their antivirus software and practice safe surfing habits. Other counter measures such as patching and regular backups, are also essential for keeping your systems safe from rootkits.
At ExterNetworks, we understand the importance of staying one step ahead in the ever-evolving landscape of cyber threats. With our proactive monitoring services, you can rest easy knowing that potential threats are being identified and addressed before they can impact your organization. Our team of cybersecurity experts brings years of experience to the table, ensuring that your systems are always protected against the latest threats.
We offer customized solutions to fit your unique cybersecurity needs, ensuring you receive the level of protection your organization requires. Additionally, we help keep your organization compliant with industry regulations and standards, giving you peace of mind knowing that your data is secure.
By choosing ExterNetworks for cyber threat monitoring services, you can save on the costs of hiring an in-house security team while benefiting from top-notch protection. Don’t wait until it’s too late—contact ExterNetworks today to learn more about how our services can benefit your organization.
