28.4k views
Cyber security is one of the most critical aspects of running a modern enterprise. Vulnerability assessments are used to identify potential weaknesses in computer systems and networks, and they can also evaluate existing systems and networks to determine whether changes are needed. Learn more about vulnerability assessments and see why they’re important.
Vulnerability assessment (VA) is a process that identifies vulnerabilities within networked computing devices or applications. It involves identifying software flaws that could allow hackers to access sensitive information or disrupt operations. VA helps organizations understand their risks to take steps to prevent them from happening.
Vulnerabilities can occur when there’s a flaw in a system’s design, programming, or configuration. Examples include Software bugs, Poorly configured servers, Security holes in programs etc. The best way to assess a system’s risk level is by performing a thorough review of all its components.
Vulnerability assessments provide information about the security posture of an organization. This includes identifying weaknesses in software, hardware, network infrastructure, and organizational processes. The results from a vulnerability assessment can then be used to prioritize remediation efforts.
A vulnerability scan will look for known vulnerabilities in your network. It could find out if any of your systems are vulnerable to viruses, worms, spyware, or other types of malware. It might also identify weak passwords, outdated software, and unpatched security holes.
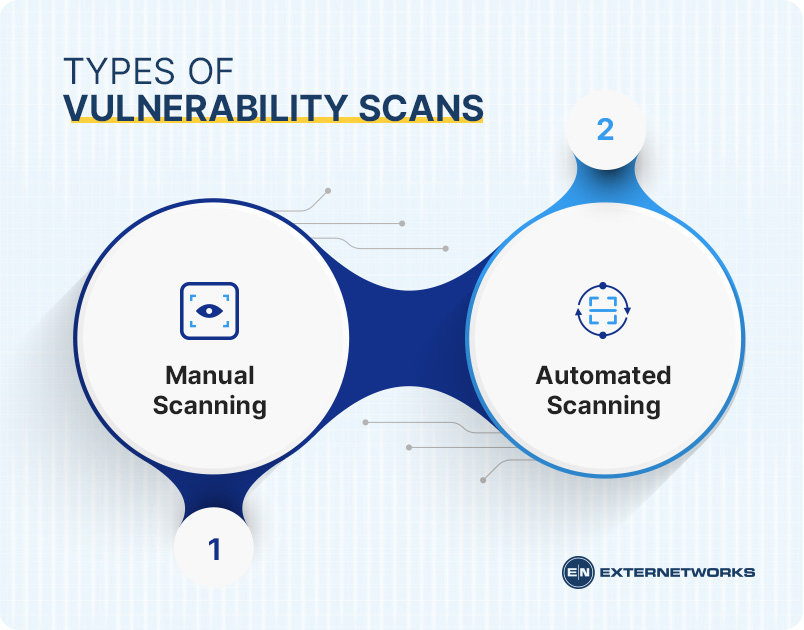
Vulnerability scans are often performed using one of two methods:
Some vendors offer both manual and automated scanning tools, and some only offer one type.
Security professionals use vulnerability assessments to ensure that their company’s computers and networks are safe. They do this because many cyberattacks start with someone gaining unauthorized access to a computer. Once inside, they can steal valuable information, damage files, and even shut down entire systems.
Vulnerability assessments can help you identify potential weaknesses in your network before they become significant problems. For example, you may discover that some of your employees’ laptops have been infected with viruses, and you can then address those infections before they cause serious harm.
Vulnerability assessments can also help you determine whether your current cybersecurity measures are adequate. If you’re unsure how well your defenses are working, you can perform a vulnerability assessment to see what weaknesses you need to fix.
A VA consists of three main components:
VA involves several phases:
Pre-assessment – This phase includes identifying all of the assets that need to be assessed, and it also involves planning and gathering the resources required to complete the assessment.
Assessment – The actual assessment process begins when you send out a request for proposals (RFP) to vendors who specialize in performing VA. Vendors respond with a proposal detailing how they would assess each asset identified in the RFP.
Post-Assessment – After receiving vendor responses, you review their proposed solutions and select one vendor to perform the VA. Once the VA is completed, you evaluate the results and decide what actions you want to take based on the findings.
It’s critical to identify vulnerabilities as soon as possible so that you can take steps to prevent hackers from using them. Hackers are constantly looking for ways to gain access to systems. When they find a weakness, they try to figure out how to exploit it.
If you don’t know which parts of your infrastructure are vulnerable, you won’t be able to stop hackers from taking advantage of them. That means you’ll likely face an increased risk of loss, fines, and lawsuits.
You can hire an external company or use internal staff members to perform a VA. A VA performed by an outside firm typically takes longer than one conducted by internal staff because it requires additional time to gather information and analyze the results. However, an external firm may provide better quality results because they have experience conducting vulnerability assessments.
Conclusion
In conclusion, vulnerability assessment is very important as it helps us know our network status and gives us the confidence to say that we are secure enough. The most important thing to remember is that cyber security is not just about keeping your computer safe from viruses. It’s also about protecting yourself against hackers who want to steal your personal information, identity theft, and financial fraud.
Ensure that your systems remain safe and secure with our Network Monitoring Services to save time and cost.
