28.4k views
A Network Vulnerability Assessments (NVA) is a method of identifying potential threats to a company’s asset across applications, and network infrastructure. This involves testing the network security issues and finding out where weaknesses exist. Network security is important because hackers can access sensitive information stored on computers connected to the Internet.
Malicious Hackers can also steal data from businesses and individuals through cyber attacks.These potential Vulnerability helps companies prevent security breaches and reduce the potential risk of being hacked.
How do you identify network vulnerabilities? Is it possible to hack into someone else’s computer or network without knowing their password?
The term “Network Vulnerability Assessments refers to a process that identifies security vulnerabilities and potential security risks within a company’s internal network. IT professionals often use it, but anyone with access to the network can perform this task.
Network vulnerability scanners will performed by network administrator in organizations that want to ensure that their networks threats are secure. These vulnerability scans look for weak passwords, outdated software and unpatched systems, and they also check for misconfigured devices.
An Network vulnerability will done during the initial setup of a new device networks or when an existing device needs to be updated. It may also be performed periodically to ensure that no new vulnerabilities were introduced into the network.
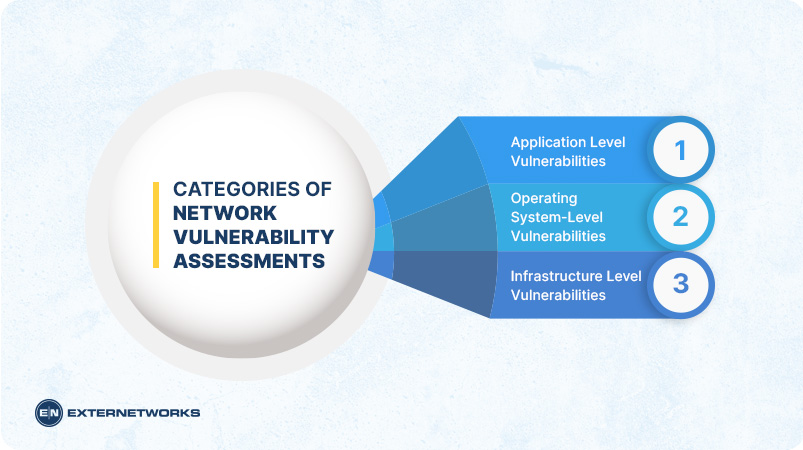
Network Vulnerability Assessments fall under three main categories:
Application Level Vulnerabilities – These are vulnerabilities that affect the programs running on the network. Examples include SQL injection, cross-site scripting, buffer overflows attack, etc.
Operating System-Level Vulnerabilities – These vulnerabilities affect the operating system itself. Examples include privilege escalation, local root compromise, etc.
Infrastructure Level Vulnerabilities – This category refers to vulnerabilities that affect the hardware infrastructure of the network. Examples include misconfigured firewalls, unpatched vulnerabilities software, etc.
Your business depends on its IT infrastructure, but it also relies on computers and other electronic devices that can be vulnerable to phishing attack. A Network for Vulnerability Assessments identifies weaknesses in your organization’s information technology system so you can take steps to protect against Malicious hackers.
The process for conducting a Network Vulnerability Assessments involves:
Penetration testing is a form of hacking focused on discovering vulnerabilities, and it is often used as part of a larger project designed to improve an organization’s security. Penetration tests will performed by experienced professionals who use specialized vulnerability assessment tools to uncover hidden flaws in a network.
Penetration testers may attempt to gain access to sensitive areas of a network, such as databases or web servers. They may try to exploit known vulnerabilities or create new ones and this penetration tests help find vulnerabilities, they don’t always provide actionable insights into how those vulnerabilities could be exploited.
Network Vulnerability Assessments look at all aspects of an organization’s network, including hardware, software, operating systems, applications and protocols. Potential vulnerabilities test help organizations understand which parts of their network are most vulnerable to attack by examining these components.
There are several ways you can perform an Network Assessments. Some of these methods include:
Scanning is one of the most popular methods of performing Vulnerability Assessment of network because it allows you to quickly identify weaknesses within your network. However, it does have limitations. For example, you won’t know where the defects are located on the network.
Penetration Testing – This approach is similar to scanning in that you send packets of information across the internet looking for weaknesses. However, there are differences between the two. With penetration testing, you’ll try to break into the network using techniques such as phishing or spear phishing.
Vulnerability Scanning – This is another way to perform an scanning. Here, you use vulnerability scanning software tools to search for known vulnerabilities in the network.
Social Engineering – This method is also called “social hacking”. In this case, you’ll use human intelligence to gather information about the network.
In addition to the above methods, you can also perform an Vulnerability Assessment of network using other means. These include:
Physical Security Audit – If you suspect that someone might gain unauthorized access to your network, you can perform a physical audit. This includes checking for physical flaws such as doors left open or windows broken.
Log Analysis – Another way to perform a Vulnerability Assessment of network is to review logs. This could involve reviewing firewall logs, application logs, or server logs.
Malware Detection – If you suspect malware is present on your network, you can scan it with anti-malware tools.
Intrusion Detection – If you suspect that your network is being attacked, you can monitor it using intrusion detection tools.
Malware Remediation – If you detect malware on your network, you need to remove it.
Data Loss Prevention – If you suspect data theft has occurred, you can use data loss prevention tools to prevent further losses.
Data Breach Investigation Response – If you discover that sensitive data has been stolen, you can investigate the incident and respond accordingly.
Security Information Event Management – SIEMs allows you to collect all relevant security events and correlate them together to help you understand what happened in real-time.
The benefits of conducting an Vulnerability Assessment of network depend on how much organization at risk you’re willing to accept. You’ll want to consider these factors when choosing the best approach for your organization.
Cost – A full Network Vulnerability will cost more than a partial Network Vulnerability . However, if you have a large network, it may be worth paying for a complete Network Vulnerability Assessment.
Time – Conducting an Network Vulnerability takes longer than performing a simple scan. However, it provides greater detail and insight into your network.
Scope – A full Network Vulnerability covers a wide range of devices and services. On the other hand, a partial Network Vulnerability only looks at specific devices and services.
Accuracy – Provides a detailed report showing where problems exist within your network.
Reliability – This allows you to find issues and take action quickly.
Compliance – A full Network Vulnerability meets compliance requirements.
Scalability – It Can be performed over a long period.
In conclusion, Network Vulnerability Assessments (NVA) is how you determine whether your network is secure against malicious attacks. It involves identifying possible weaknesses in your network and then taking steps to fix them. The goal of any Vulnerability is to ensure that no single point of failure exists on your network.
You can conduct an Network Vulnerability using many different approaches, and each process has its strengths and weaknesses. Therefore, it’s important to choose the right method based on your needs.
