28.4k views
In a digital age where cyber threats lurk around every virtual corner, can we truly trust anyone or anything? As organizations navigate the complex data security landscape, a paradigm shift toward a Zero Trust Architecture is gaining traction.
Gone are the days when perimeter security alone was sufficient to safeguard sensitive information. Traditional security models have proven ineffective against sophisticated cyber attacks, leading to the emergence of the Zero Trust approach, which challenges the concept of trust within digital ecosystems.
Zero Trust Architecture operates on the principle of “never trust, always verify.” Organizations can mitigate risks and enhance their security posture by assuming that threats exist inside and outside the network. Implementing a Zero Trust framework has become imperative as businesses strive to protect their assets and data from malicious actors. Let’s delve deeper into the key tenets and benefits of Zero Trust Architecture in the realm of cybersecurity.
Zero Trust Architecture is a powerful cybersecurity strategy that shifts the traditional approach of assuming trust within a network to one of continuous verification. By applying security policies based on context, such as user roles, device information, and location, organizations can greatly enhance their defense against cyber threats. This approach ensures that only authorized users have access to specific resources and data, minimizing the risk of unauthorized access and lateral movement within the network.
Furthermore, implementing a well-tuned zero trust architecture enhances security, simplifies network infrastructure, and improves the user experience. The “never trust, always verify” principle underscores the importance of constantly validating identities and permissions to prevent potential security breaches. By closely monitoring traffic, enforcing robust authentication methods like Multi Factor Authentication (MFA), and focusing on context-based access controls rather than relying on network location alone, organizations can create a robust security framework that adapts to evolving cyber threats. Ultimately, Zero Trust Architecture offers a proactive approach to cybersecurity that effectively mitigates risks and protects critical assets in today’s increasingly complex digital landscape.
As organizations continue to evolve and adopt new technologies, the traditional hub-and-spoke network architecture with its castle-and-moat security model is no longer adequate. The shift towards cloud services, mobility, and other digital transformations have created new challenges in terms of data security and access control. The need for a more secure, agile, and efficient network architecture has never been more crucial as organizations strive to stay ahead in today’s rapidly changing technological landscape.
Zero Trust Architecture offers a solution to these challenges by assuming that attackers are already inside the network rather than trusting any user or device based on their location. This approach emphasizes continuous verification of trust, least privilege access controls, and strict authentication protocols to ensure that only authorized users can access resources.
By implementing Zero Trust Architecture, organizations can enhance their security posture, reduce the risk of data breaches, improve agility in adapting to new technologies, and streamline access to applications across various environments such as on-premises data centers and cloud services. As digital transformation continues to accelerate, adopting Zero Trust Architecture is essential for organizations looking to modernize their networks while maintaining a high level of cybersecurity.
Zero trust architecture operates on the fundamental principle of never trusting any entity on the network and always verifying their identity, device posture, and business context before granting access. This approach recognizes that traditional security measures are no longer sufficient to protect against sophisticated cyberattacks in today’s threat landscape. By assuming that everything on the network is hostile or compromised, zero trust ensures that all traffic is logged, inspected, and subjected to a stringent verification process before allowing connections.
A key component of a true zero trust architecture is a proxy-based system that connects users directly to applications instead of the network. This design enables additional controls to be applied before connections are either permitted or blocked, providing an extra layer of security. The three-step process involved in establishing a connection in a zero trust architecture—verifying identity and context, controlling risk, and inspecting traffic for threats and data—ensures that every interaction on the network is carefully monitored and evaluated to mitigate potential risks. By implementing these principles, organizations can enhance their cybersecurity posture and better protect their sensitive information from malicious actors.
Zero trust architecture is a cybersecurity framework that assumes organizations should not automatically trust any user or device inside or outside their perimeters. The five pillars of zero trust, as outlined by CISA, provide a comprehensive roadmap for implementing a more secure and resilient network infrastructure.
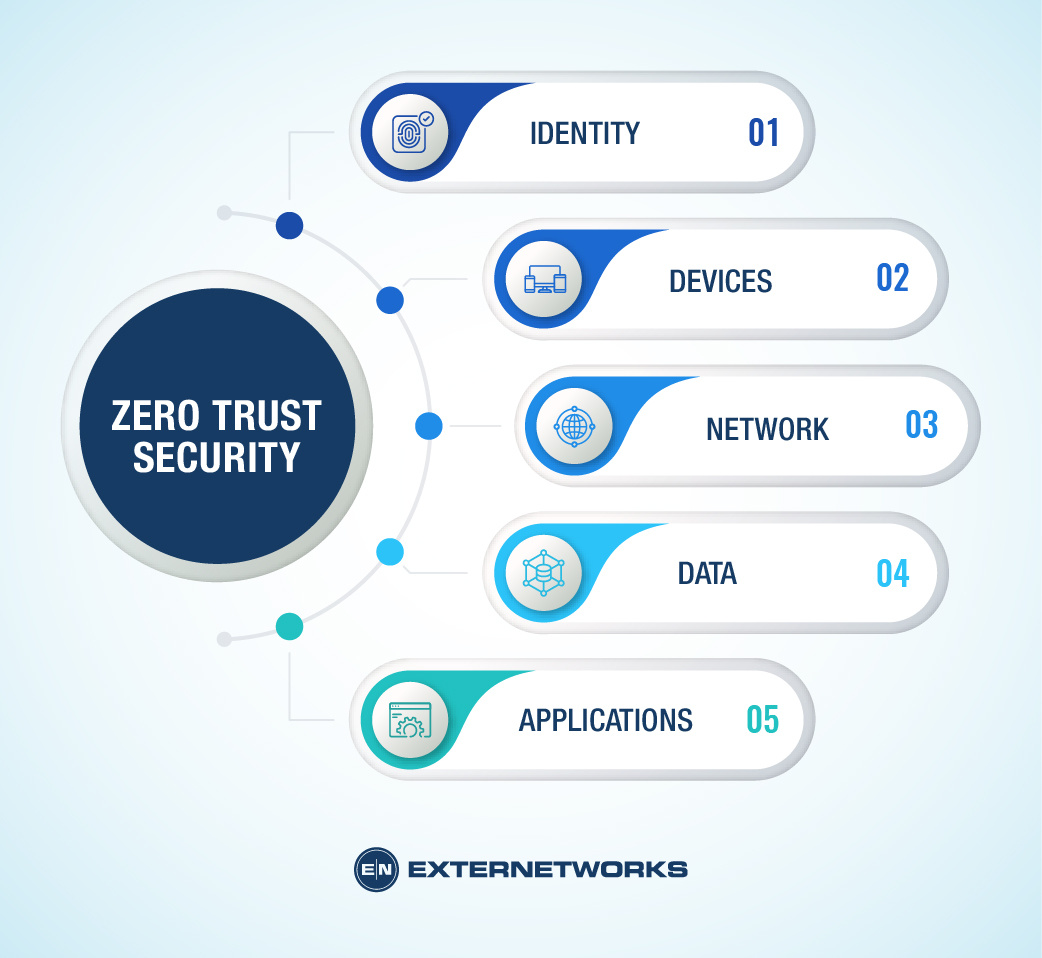
The first pillar, identity management, emphasizes the importance of adopting a least-privileged access approach to limit potential security risks associated with excessive user permissions. Organizations can reduce the likelihood of unauthorized access to critical systems and data by closely managing user identities and access controls.
The second pillar focuses on devices and ensuring the integrity of devices used to access services and data. Organizations must implement robust security measures, such as endpoint protection solutions and device compliance checks, to prevent potential threats from compromised devices. The third pillar emphasizes network segmentation based on application workflows rather than traditional perimeter-based approaches. This granular segmentation allows organizations to control network traffic better and restrict unauthorized access within their network environments.
The fourth pillar of zero trust architecture addresses data protection and encryption to safeguard sensitive information from unauthorized access or data breaches. Organizations can ensure that data remains secure at rest and in transit by implementing encryption protocols and monitoring data flows. This pillar also emphasizes the importance of continuous monitoring and threat detection to identify and respond to potential security incidents in real time. Additionally, the fifth pillar highlights the importance of integrating security protections into applications and workloads to ensure that access is granted based on multiple attributes such as identity, device compliance, and behavior analysis.
Choosing a Zero Trust Architecture (ZTA) offers several key benefits, particularly enhancing security and managing risk in modern IT environments. Here are the primary advantages:
Adopting a Zero Trust Architecture is a strategic move towards modernizing security postures, protecting critical assets, and ensuring robust and scalable security in an increasingly complex and distributed IT landscape.
Zero trust architecture represents a significant advancement in security measures over traditional models due to its proactive and adaptive nature. By constantly validating user identities and device security postures, zero trust goes beyond the limited protection offered by perimeter defenses. Implementing granular least-privileged access controls ensures that users and devices are only granted access to the bare minimum necessary for their tasks, reducing the potential attack surface. Moreover, continuous monitoring, multi-factor authentication (MFA), and behavioral analytics enable real-time threat detection and response, preventing successful attacks before they can cause harm.
Additionally, the versatility of zero trust architecture makes it better equipped to handle the evolving cybersecurity landscape shaped by remote work and cloud computing. Its data-centric focus ensures that sensitive information is protected regardless of where it resides or travels within the network environment. This adaptability also allows zero trust to address novel vulnerabilities more effectively than traditional models, providing a more agile defense against emerging threats. In conclusion, zero trust architecture emerges as a superior choice for today’s cybersecurity needs as it prioritizes data protection, enacts robust access controls, and employs cutting-edge technologies for proactive threat mitigation.
Why Choose ExterNetworks
ExterNetworks is a trusted partner for organizations looking to implement a Zero Trust Network Security Model. With extensive experience in cybersecurity solutions, ExterNetworks offers tailored services that align with your specific security needs and goals. Our team of experts will work closely with you to design and deploy a robust zero trust architecture that protects your critical assets while enabling seamless access for authorized users.
Additionally, ExterNetworks prioritizes ongoing support and monitoring to ensure the effectiveness of your security measures, providing peace of mind in an ever-changing threat landscape. By choosing ExterNetworks as your cybersecurity partner, you can rest assured that your organization is equipped with the latest security technology and best practices, safeguarding your data and infrastructure from potential threats.
ConclusionAdopting a Zero Trust Architecture is essential for organizations looking to enhance their security posture and protect critical assets in today’s evolving threat landscape. By moving away from traditional security models towards a more proactive and adaptive approach, organizations can better defend against sophisticated cyber threats and ensure their data’s confidentiality, integrity, and availability.
ExterNetworks offers comprehensive cybersecurity solutions tailored to your specific needs, providing expert guidance and support throughout the implementation process. With enhanced visibility, control, and data protection capabilities, zero trust architecture emerges as a superior choice for organizations seeking to strengthen their cybersecurity defenses and stay ahead of evolving threats. Choose ExterNetworks as your trusted partner in safeguarding your data and infrastructure with cutting-edge security technology and best practices.
